Readers,
One of the big trends our firm is tracking into 2026 is the convergence of specific elements of Cloud Security and Security Operations because of the rise of AI Agents. The focus is moving toward runtime as opposed to posture. Contrarian, but it’s the reality.
Let’s be clear: these are two different teams within each organization today. However, this year we’ve started to see big pushes to help both fragmented teams understand. Fun fact: In most enterprise SOC (SIEM) environments, the highest-volume alert sources consistently come from endpoint security tools and identity systems, but increasingly, cloud-native alerts are the fastest-growing sources contributing to SIEM noise. As organizations migrate workloads to AWS, Azure, and GCP, misconfiguration findings, IAM privilege anomalies, workload runtime events, and CSP-native threat detections increasingly dominate the alert landscape. This shift is pushing cloud security signals closer to the top tier of SIEM alert sources, transforming them from a secondary feed into a primary operational driver for modern SOCs.
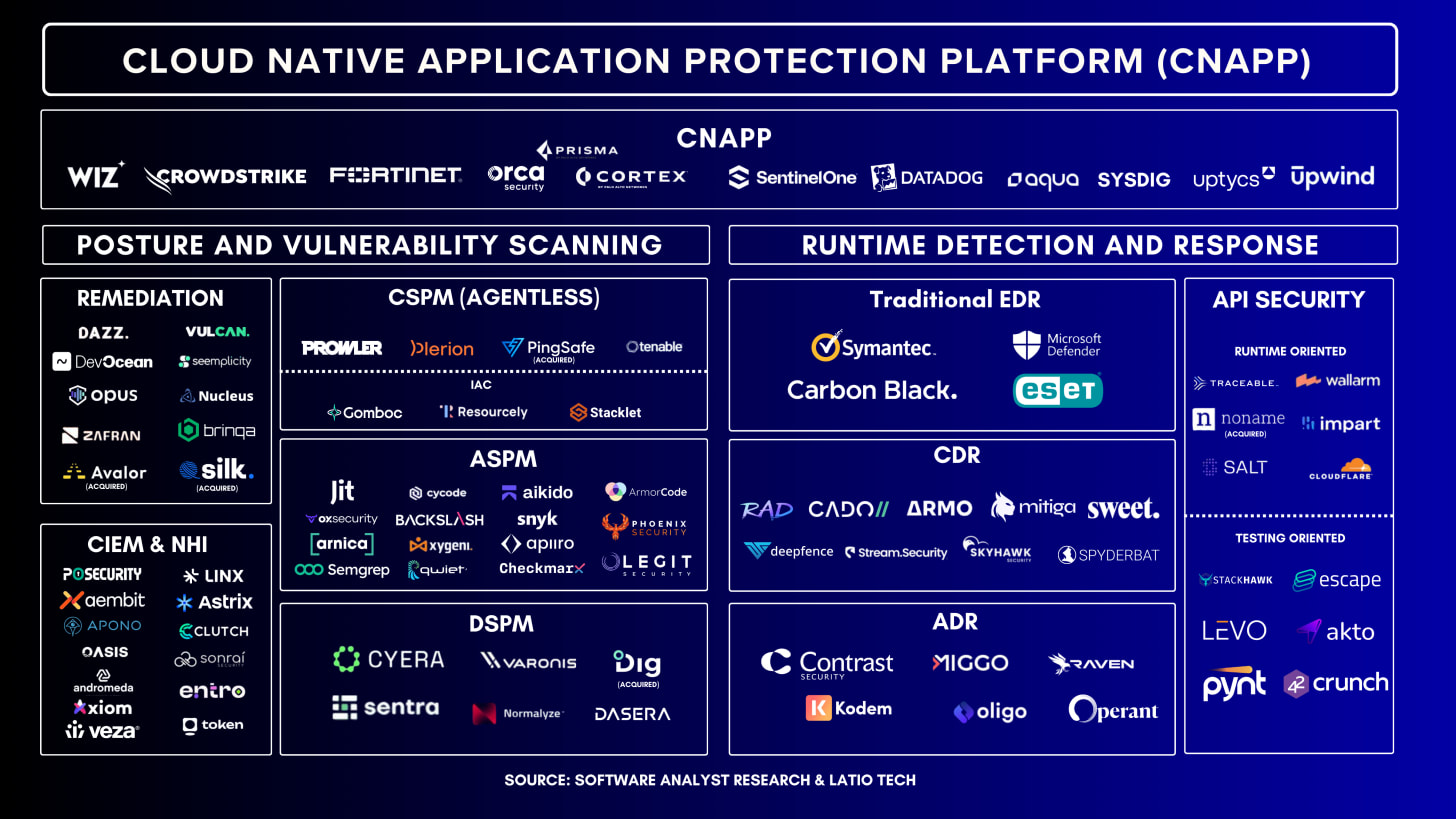
Earlier this year, my colleague, James Berthoty, and I wrote an in-depth analysis on the rise of CNAPP. As you can see, we clearly distinguish between the cloud posture scanning vs. runtime detection controls.
Understanding the Difference Between Cloud Security and SOC Teams
In most organizations, cloud security teams focus on proactively designing, securing, and governing cloud environments: building preventive guardrails, vulnerability policies, managing cloud configurations, and ensuring workloads are architected securely.
In contrast, Security Operations Centers (SOCs) specialize in real-time threat detection, incident response, and continuous monitoring across the entire enterprise. While cloud security engineers work “left of boom” by embedding controls into infrastructure and development pipelines, SOC analysts work “right of boom,” reacting to alerts, investigating anomalies, and containing active threats. These parallel missions create different rhythms, skill sets, and operational priorities, even as both domains increasingly overlap in the modern cloud-first enterprise.
The Case For Convergence
Many who argue for the case for convergence will say that cloud platforms now generate the majority of an organization’s telemetry, identity events, and configuration drift, blurring the line between engineering and operations. As a result, fragmented ownership often slows investigations, creates blind spots, and forces SOC teams to rely on cloud specialists for basic context.
Converging the functions or at least integrating them more tightly creates end-to-end visibility from cloud misconfigurations to active threat activity. It also shortens response times by allowing analysts to understand cloud-native logs, identities, and architectures without excessive handoffs.
For engineering teams, convergence ensures that secure design is informed by real-world attack patterns, enabling guardrails and policies rooted in operational threat intelligence rather than theoretical best practices. Ultimately, convergence promises unified tooling, shared situational awareness, and a more resilient defense posture aligned with how attacks actually unfold in cloud environments.
The Case Against Convergence
Despite the appeal, full convergence risks collapsing two highly specialized disciplines into a single overloaded function. Cloud security demands deep architectural expertise: understanding K8s, managing Terraform modules, IAM policy evaluation logic, Kubernetes internals, multi-account governance frameworks, and cloud service quirks that change monthly.
SOC operations, meanwhile, require mastery of threat hunting, detection engineering, triage workflows, and incident command. Expecting a unified team to excel at both may dilute depth, hinder skill development, and lead to surface-level coverage rather than true expertise. Organizationally, blending the functions can also create unclear ownership of remediation, stretch response teams into engineering domains they are not equipped to modify, and reduce the strategic focus on long-term cloud risk reduction. In some cases, maintaining healthy separation preserves accountability, specialization, and the ability to scale each capability according to its unique demands.
Webinar To Address The Debate & Convergence
I’m excited to announce that our firm will host a webinar session, which dives into a critical topic for every CISO today: the convergence of cloud security. In this exclusive executive webinar, join a select group of global CISOs for a discussion led by our very own Aqsa Taylor, Chief Research Officer at SACR.
This live session brings together senior security leaders from major enterprises to share real-world strategies, emerging priorities, and practical guidance on how to strengthen modern defense programs. Together, the panel will dive into the issues shaping the CISO’s agenda in 2026, including:
-
How to close visibility gaps between cloud environments and the SOC
-
Understanding the case for and against convergence
-
Top leadership priorities for cloud security defense
-
Where AI fits across threat detection, response, and program efficiency
-
What it takes to unify teams across security, engineering, and operations
-
Building resilience across hybrid and multi-cloud environments
This is a rare opportunity to hear directly from Fortune 500 CISOs on their cloud security strategy.
Reports on the convergence of Cloud and SOC
Palo Alto Networks is attempting to pull off this convergence in its Cortex Cloud. In a recent deep dive on the future of cloud and security operations, I examined how the traditional divide between cloud security teams and SOC functions is being challenged by evolving threat patterns and platform strategies, most notably through Palo Alto Networks’ launch of Cortex Cloud.
The report traces how cloud security began as posture scanning and misconfiguration detection, while SOC teams focused separately on runtime threat detection and incident response. As cloud environments grow more complex, alert volumes from cloud-native platforms have surged, exposing gaps. Cortex Cloud represents a strategic attempt to unify CNAPP-style posture, runtime, identity, and vulnerability data with SIEM/XDR/SOAR capabilities on a single data plane, enriched by AI and automation to reduce context switching and mean time to respond. While this convergence offers operational efficiencies, improved visibility, and a holistic risk context tied back to CI/CD and source code, the report also highlights that seamless cross-team workflows and clear ownership remain significant challenges. Ultimately, Palo Alto’s move illustrates both the promise and the complexity of aligning cloud security and SOC operations, showing why platform approaches and integrated tooling are at the center of the convergence trend.
Summary
The industry is entering a phase where cloud complexity, identity sprawl, and AI-accelerated threats are rewriting the rules of modern defense. Whether convergence is the right model for a given enterprise will depend on its maturity, architecture, and talent structure. But ignoring the shift is no longer an option.
Cloud alerts are becoming operational signals, SOC teams are leaning deeper into cloud contexts, and engineering leaders are being pulled into incident response cycles they’ve never owned before. This is the moment for security leaders to recalibrate, challenge assumptions, and build programs that can operate at cloud speed. Our executive webinar is designed to help CISOs do exactly that, by bringing clarity to a conversation that is often framed as binary, but in practice, is anything but.