Actionable Summary
Despite decades of investment in IAM, IGA, and PAM, enterprises remain highly vulnerable to identity-based attacks. The root cause is not policy failure, but implementation failure. We’re introducing the concept of Identity Dark Matter.
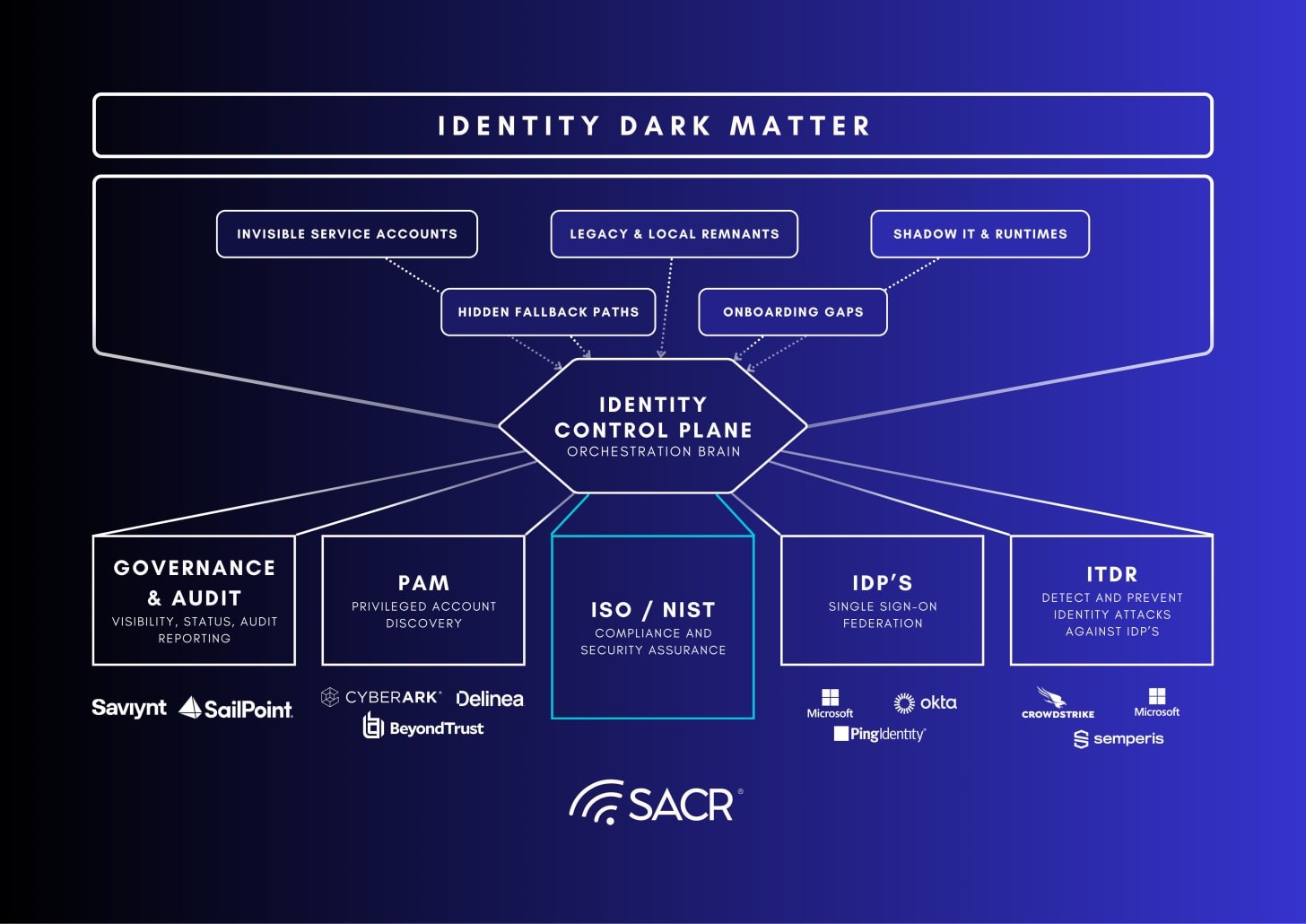
This research defines Identity Dark Matter as the unmanaged identity artifacts within an enterprise stack: i.e., local accounts, legacy authentication fallbacks, orphaned service accounts, API keys, and application-level entitlements that operate outside centralized governance. Threat actors increasingly exploit these blind spots to bypass SSO, evade MFA, move laterally, and escalate privileges without triggering traditional identity alerts. This report introduces this new identity control plane as a new architectural layer designed to close the gap between intended policy and effective access by correlating runtime telemetry, identity context, and automated remediation across managed and unmanaged identities.
Modern identity security is compromised by unmanaged ide
ntity artifacts operating outside centralized governance (IGA/IdP/PAM) systems. This security gap is exploited by threat actors for lateral movement, bypassing SSO, and escalating privileges, fundamentally undermining compliance (SOX, GDPR, etc.).
Modern enterprises also face a critical disparity, while organizations invest heavily in centralized systems to lock the front door, attackers are increasingly exploiting the unhappy paths of the identity ecosystem. This unmanaged attack surface is often the identity dark matter that we all need to pay attention to.
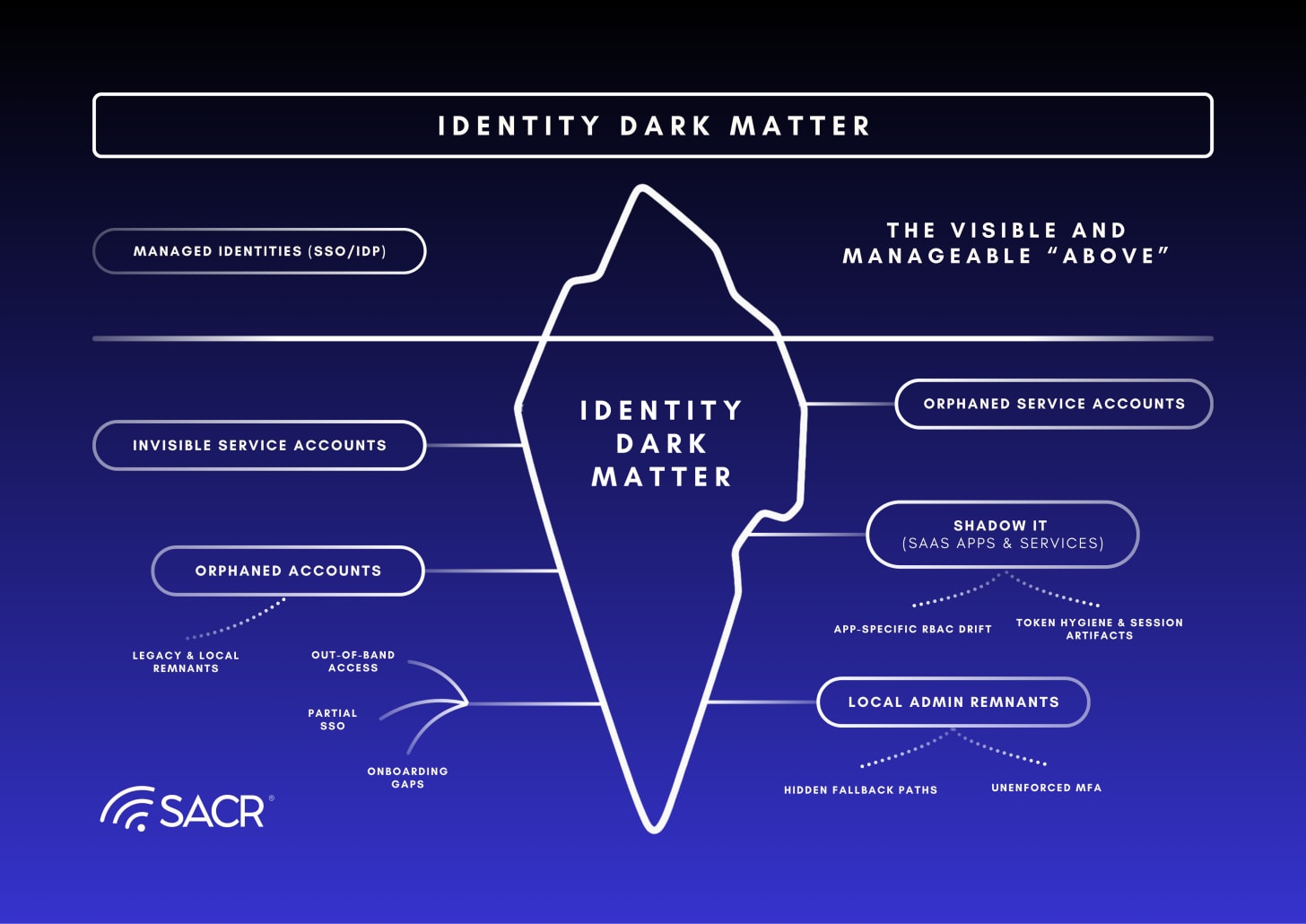
The composition of identity Dark Matter includes a fragmentation of various risks resulting from both technical debt and rapid cloud and application adoption along with tech debt resulting from old systems and applications that have been deployed, but running in the corner that need proper maintenance and visibility.
-
Hidden Fallback Paths: Applications that are installed by business line employees or improperly managed can lead to local account use, hard-coated credentials that often bypass policies such as multifactor authentication creating significant risks of authentication bypass to the enterprise.
-
Orphaned Non-Human Identities: service accounts and API keys that have been issued for decommissioned applications often are left un-maintained in various systems, and they often include elevated privileges that can lead to significant data breach.
-
Shadow IT adoption and Drift: Identities created outside the standard IT or organization provisioning workflows can lead to significant drift over time. Even properly provisioning processes can lead to drift, because they tend to cut corners, spread credential use across IT teams or developers as service accounts or credentials get shared or when in use after applications are retired. This is often due to the ease of developer or IT teams’ desire for deployment speed.
-
Legacy Remnants: Remnants stored on local systems and by enabled NTLM fallbacks (often called negotiation) can cause significant risks, something Microsoft has recently declared as a critical risk in their plans to end of life (EOL) in favor of Kerberos, which can cause problems on servers because they leave remnants available on endpoints and servers that attackers can exploit for lateral movement. This is a common tactic used by Scattered Spider/Scattered Lapsus$ and other threat actor groups.
Operational and Compliance Risk
The existence of dark matter creates a dangerous chasm between intended security policy and the reality of effective access and management of risks.
-
The Attack Vector: Sophisticated threat actors (e.g. Scattered Spider, Lapsus$) prioritize these unmanaged vectors for lateral movement because they do not often trigger standard IAM and authentication alerts. Attacks like SolarWinds compromised systems in this manner, coupled with discovery of the environment and social engineering, highlighting the critical dangers of non-human identities and their place in the attack kill chain.
-
Regulatory Failure: Relying on centralized systems is a very good thing, however believing in comprehensive coverage without additional telemetry to confirm or deny presence of various authentication and IAM gaps creates a “compliance illusion” and could potentially lead to violations of key mandates such as NIS 2 Article 21 and other mandates and regulations for example, GDPR or SOX (which often requires strict third-party and continuous authentication). SOX requires segregation of duties because these accounts lack verifiable audit trails, you can be considered out of compliance and subject to additional fees.
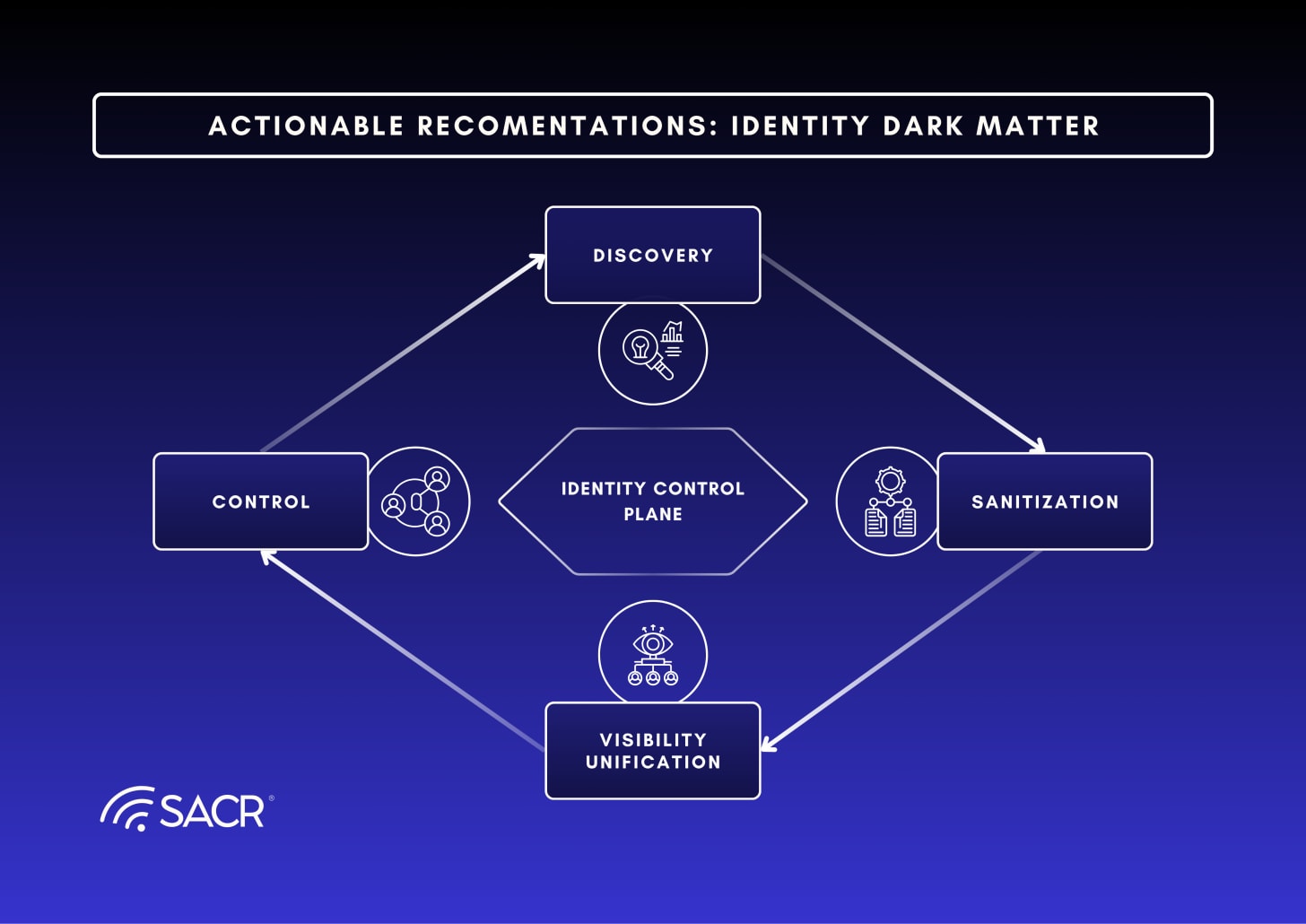
To close this gap, security leaders must shift from a strategy of consolidation, to one that emphasizes comprehensive visibility and control. We believe organizations should prioritize building an Identity Control Plane, which means they can obtain a more unified, pervasive layer for visibility and control above existing infrastructure. This plane correlates telemetry, surfaces discrepancies, and automates remediation. The strategic approach involves four phases: Discovery, Sanitization, Unification, and Control, aiming for a proactive, audit-ready Zero Trust defense against this unmanaged attack surface.
Core Functions of this Identity Control Plane:
-
Ingest telemetry: Raw access events, such as flow information, activity logs, and disk artifacts, can often reveal identity use across systems, illuminating these dark spaces.
-
Correlate context: Integrating activity data from diverse identity systems- managed and unmanaged- is beneficial. For example, privileged service accounts managed by a PAM solution on local machines might be poorly managed elsewhere. Analyzing all activity across applications can uncover critical relationships, providing key insight or suggesting unmanaged identity use.
-
Surface Findings: Organizations must use reports and reviews to find critical risks. LLMs and graph databases enable identity professionals to quickly identify threats, escalate findings for remediation, and deeply examine potential attack paths.
-
Enable Action: Automated analysis and correlation of IAM data can significantly address enterprise identity dark matter, saving practitioner time on remediation, providing greater context for risk reduction.
Actionable Recommendations for CISOs
Leverage a phased approach to gaining visibility and control of Identity Dark Matter. These phases include:
-
Phase 1: Discovery (Visibility First): Do not block access initially. Deploy a pilot to instrument critical applications and detect local account usage and bypass attempts.
-
Phase 2: Sanitization: Systematically eliminate legacy protocols (NTLM) and vault orphaned service account credentials.
-
Phase 3: Unification: Route authenticated traffic through the Identity Control Plane to enforce continuous evaluation.
-
Phase 4: Control: Establish the Control Plane as the central enforcement point for dynamic governance over both managed and unmanaged identities.
Introduction
The thesis of this research proposes that an expanding Identity Dark Matter has permeated enterprises. This emerging challenge encompasses all identity-related artifacts, credentials, and access pathways present in a typical enterprise IT environment that are neither visible to nor managed by centralized governance systems (IGA/IdP/PAM) and identity processes. This “identity dark matter” represents the critical disparity between an organization’s intended security policy and the actual effective access that should exist and be the primary goal of most IAM programs. In the complex landscape of modern cybersecurity, this silent but pervasive threat lurks.
According to Orchid Security, Enterprises have an average of ~1,200 applications, each with their own identity implementations, with 48% of it falling outside of IAM systems and constituting Identity Dark Matter. We must discover, identify and remediate such Identity Dark Matter in order to take back control of our enterprise identities, access and entitlements in order to maintain consistent security measures.
This report proposes a new concept of using a control plane and a defined taxonomy and approach to suss out new and often hidden risks and introduces to readers, an emerging methodology and technology for assessment and transition to an Identity Control Plane. The report also defines a taxonomy for identity dark matter as well as proposes a new control plane concept to bring it into the light, so that intended security policy can be fully implemented.
Cloud Sprawl, Legacy Applications, Self-Hosted Applications Lead To Greater Risks to Identity
The concept of Identity Dark Matter encompasses elements often-overlooked, like collections of identity-related artifacts that operate completely outside the scope of an organization’s formal Identity Governance and Administration (IGA), Identity Provider (IdP), Privileged Access Management (PAM) and other identity systems. SaaS based offerings adopted with personal accounts (for example Shadow IT) complicates matters, but are more easily integrated into IAM systems during remediation efforts. The Identity Dark Matter creates a dangerous chasm between the intended security posture and the reality of effective access, dramatically increasing the attack surface and making robust identity defense nearly impossible. Understanding and mitigating this very real and often invisible threat is the first critical step toward achieving true security in the age of pervasive digital identities.
Attackers have Shifted to “Shadow IT” SaaS, Cloud then pivot to our Premises
Attackers actively target and exploit these invisible vectors rather than focusing on the often more hardened Single Sign-On (SSO) login. We argue that to truly secure identity, organizations must look beyond the managed and visible surface area of well known systems and focus more than on the Identity and Access Management (IAM) veneer. True identity resides deeper, within the code, in the source, that’s where this new Identity Dark Matter often exists. And it is dangerous.
-
The Paradox: Despite massive investment in Identity Access Management (IAM), organizations still often remain vulnerable. The “front door” is locked, but attackers are bypassing it entirely through unmanaged, invisible vectors, often introduced in code or entitlements.
-
The Concept: We define this unseen risk as Identity Dark Matter. Identity Dark Matter2 is defined as the vast accumulation of hidden fallback paths, SaaS entitlements, API keys, legacy protocols, local admin remnants, and orphaned service accounts that exist outside the view of central, integrated IdPs and managed identity systems.
-
The Findings: Current security architectures suffer from dashboard fatigue and lack of in-depth visibility into identity connectivity. They see the policy, not the reality.
-
The Recommendation: Security leaders must shift from a consolidation strategy to an “Identity Control Plane” approach. The priority is visibility first: connecting telemetry, context, and action without disrupting existing infrastructure.
Dark Matter Patterns Emerge from the Depths
Understanding and mapping these various patterns is the essential first step in building a truly comprehensive and resilient identity defense strategy.
Each organization must take a more proactive approach to identify and focus on.
-
Unmanaged Legacy applications, Cloud apps and Shadow IT applications: Create gaps in visibility, control and governance leading to blind spots for IAM programs.
-
Hidden Fallback Paths and Unenforced MFA due to IdP Bypass: “Break-glass” local accounts or secondary authentication mechanisms hardcoded into applications that bypass the primary IdP. Any authentication path, such as legacy VPN or administrative jump boxes, that permits a user to log in successfully without the mandatory Multi-Factor Authentication (MFA) check enforced by the primary IdP.
-
Token Hygiene & Session Artifacts: Long-lived tokens, session hijacking vulnerabilities, and lack of continuous evaluation after initial login.
-
Legacy & Local Remnants: NTLM fallback enabled on servers, local administrator accounts left on endpoints, and shadow admins that persist after migration.
-
Orphaned Non-Human Identities: Service accounts and API keys for decommissioned apps that retain high-privilege access.
-
App-Specific RBAC Drift: Entitlements granted directly within an application (e.g., Salesforce or AWS IAM) that contradict the central IGA policy.
-
Out-of-Band Access: Contractor portals or third-party access points that do not federate through the corporate SSO.
-
Partial SSO Adoption: Applications or subsystems within a portfolio that have not been fully federated, leading to shadow directories, local accounts, and siloed credential stores outside the central IdP’s view.
-
Siloed IGA Onboarding Gaps: Discrepancies between the Identity Governance and Administration (IGA) system and the source of identity (e.g., HR system), resulting in temporary or default accounts that are provisioned without proper policy controls or timely de-provisioning.
-
Application Inventory Drift: Organizational evolution often results in application inventory drift. This drift can inadvertently generate unmanaged identities or entitlements. Such undiscovered elements remain unremediated, posing a security risk.
The Identity Sprawl Challenge
Modern enterprise identity is not a monolith, it is a fragmented ecosystem. While IAM and IGA tools manage the “happy path” of user access, they often fail to detect the “unhappy paths” created by technical debt and rapid cloud adoption. Modern enterprise identity is not a coherent, centralized monolith; it is a fragmented and sprawling ecosystem. This fragmentation is a direct consequence of decades of organic growth, mergers and acquisitions, and the accelerated shift to multi-cloud environments.
While traditional Identity and Access Management (IAM) and Identity Governance and Administration (IGA) tools are indispensable, they are inherently designed to manage the “happy path”. Traditional tools often “see” identities as directory objects, entitlements, and sessions; they do not see how each app actually implements identity outside the regimented, documented, authorized, and governed lifecycle of user access, roles, and entitlements which is much more predictable and the surface layer identity information and processes. This ungoverned territory where identities and authorizations exist without active, powerful, deep visibility and control are left invisible and unmanaged by standard identity controls and processes, this is what constitutes Identity Dark Matter. It represents a profound security gap that attackers can and do routinely exploit.
These areas are often difficult for CISO and IAM programs to get their programs around. Most IAM and IGA tools excel at provisioning, de-provisioning, and auditing access within their defined perimeters. But, these systems often fail to discover, detect and govern the “unhappy paths.”
These unhappy paths are the dark corners and ungoverned crevices of the identity landscape, created and identified as Identity Dark Matter often driven by:
-
Technical Debt: Legacy systems, abandoned or improperly decommissioned applications, and “orphaned” accounts (identities that no longer correspond to an active employee or managed resource). Inadequate visibility of identity artifacts on host systems leads to dark matter threats.
-
Rapid Cloud Adoption: The speed and decentralized nature of cloud, self-hosted applications and SaaS provisioning (SaaS, IaaS, PaaS) can often bypasses central IAM/IGA/PAM and authentication governance, leading to shadow access, over-privileged accounts, and non-human identities (service accounts, API keys) that are poorly tracked.
-
Gaps from Self-Hosted and Legacy Apps: Awareness gaps regarding self-hosted and legacy apps are a primary cause of Identity Dark Matter. When IT and security teams lack a complete inventory of these decentralized applications, the apps often use local identity stores, custom entitlements, or hardcoded credentials that bypass the central IdP. This failure to catalog and govern these systems allows unmanaged credentials and access pathways to accumulate, creating significant security blind spots that attackers can exploit for lateral movement without triggering standard IAM alerts.
The Identity and Policy Visibility Gap
A core inefficiency plaguing modern identity defense is a persistent and dangerous gap between intended policy (what the Identity Provider or IdP dictates) and actual, effective access (what the underlying network, applications, and legacy infrastructure truly allow). This disparity is the foundation upon which sophisticated attackers build their campaigns.
Attackers rarely target the high-profile, heavily hardened and often more guarded Single Sign-On (SSO) login portals, which is typically protected by multi-factor authentication and state-of-the-art security controls. Instead, they operate in the shadows, exploiting what is commonly referred to as Identity Dark Matter.
These are the critical weak points that bypass modern identity defenses, including:
-
Service Accounts with Perpetual Credentials: Accounts used by applications or services that possess non-expiring passwords, API keys, or certificates, making them a high-value, static target for persistence.
-
Legacy Authentication Fallbacks: Protocols like NTLM or basic authentication that remain enabled on older servers or applications. These are often poorly monitored and can be exploited for credential relay or brute-force attacks after an attacker has gained a minimal foothold.
-
Shadow IT adoption and Orphaned Identities: Identities created outside the standard provisioning workflow (Shadow IT) or former employee accounts that were never properly de-provisioned (Orphaned Identities) in unmanaged or self-hosted application, all of which retain undocumented access rights.
-
Over-permissioned Identities: Human or non-human accounts that, over time, have accumulated excessive and unnecessary privileges, offering an attacker far more lateral movement potential than their role requires.
-
Microservices and APIs: Identity happens in dozens of internal calls, custom JWT validation, service-to-service secrets, and sidecar patterns that no central tool fully observes.
-
Apps that implement their own authentication
-
Local user stores
-
API keys
-
“Optional” SSO integrations
-
Inconsistent MFA enforcement
-
-
Poor Modern IdP / IGA assumptions
-
IdPs assume: “If the app is integrated, my policy is enforced.”
-
IGAs assume: “If access is certified, the risk is under control.”
-
In reality, apps often:
-
Keep legacy logins or have endpoints that bypass SSO
-
Reuse or store tokens unsafely
-
Mis-handle sessions and timeouts
-
IAM programs miss identity use without host based visibility
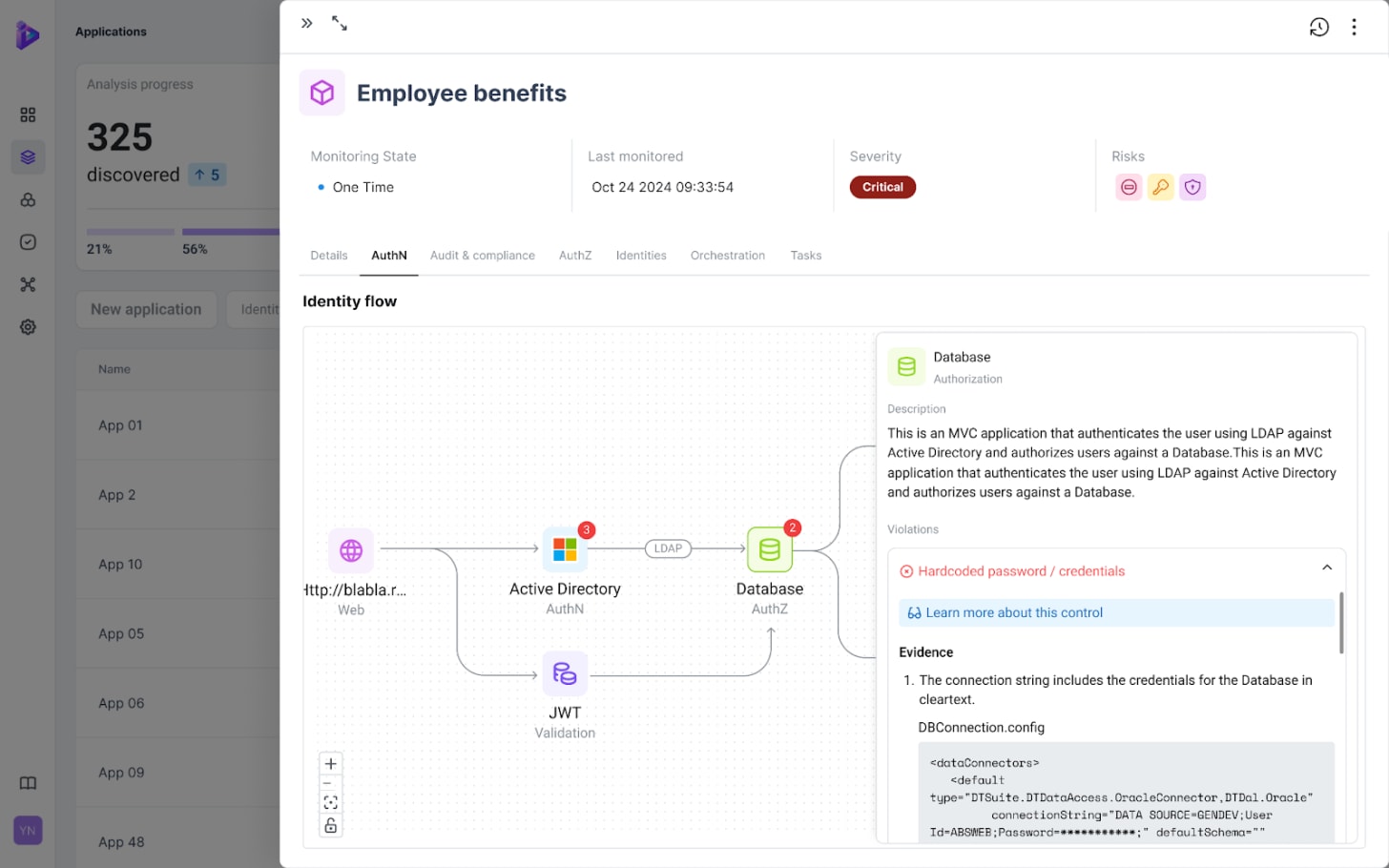
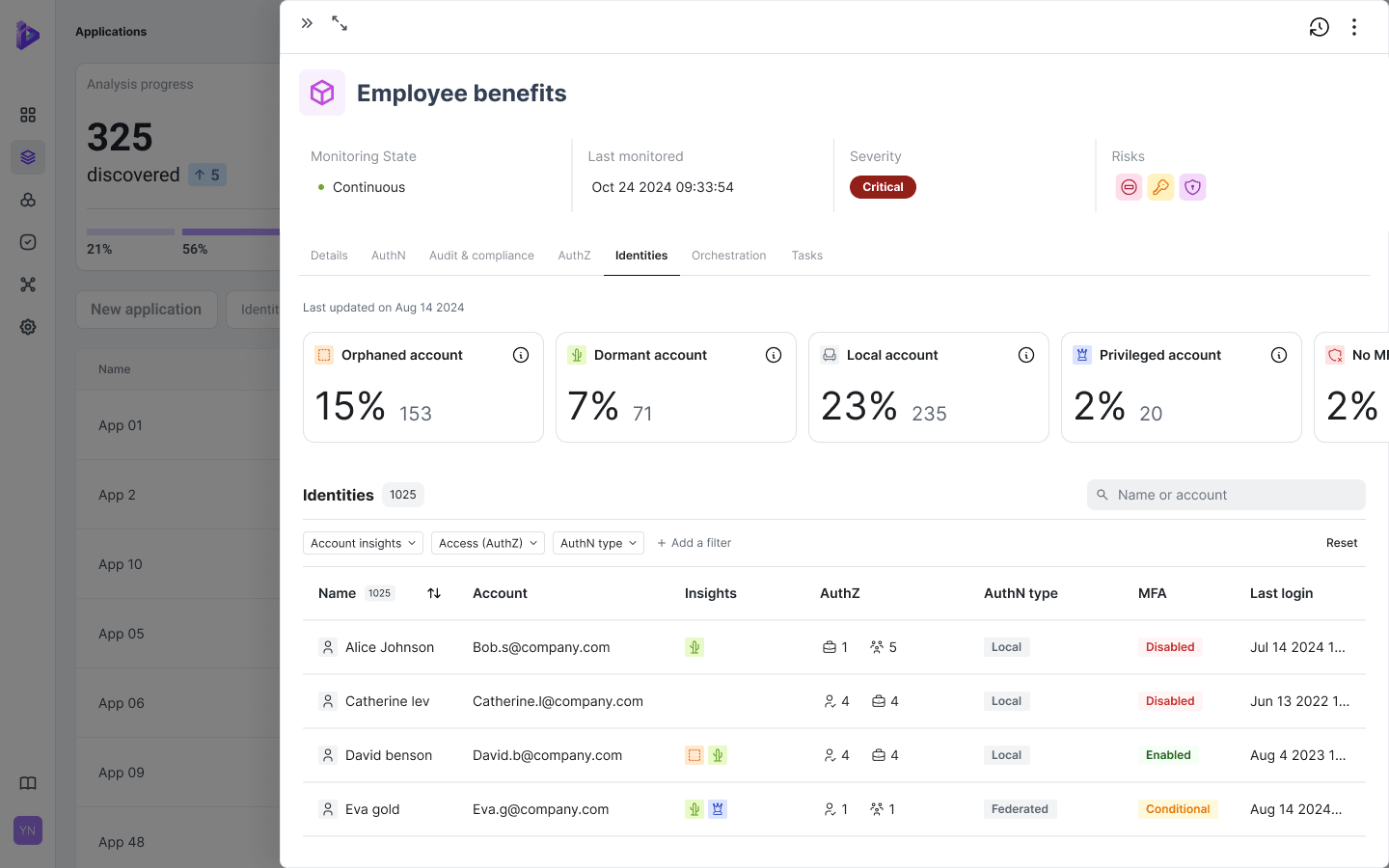
Here’s an illustration and example of Dark Matter discovery using Orchid Security:
So IAM teams and CISO’s end up with a problem
-
Central systems claiming “green” posture
-
Auditors and CISOs assuming coverage
-
Residual Compliance Issues raised by the Identity Dark Matter miss at the application level
-
Numerous unmonitored, app-level bypasses
-
Unify visibility by integrating ITSM (IT Service Management) tools and Agent-Based visibility
Compliance and Cyber Risk Implications
The presence of Identity Dark Matter fundamentally undermines an organization’s compliance posture and dramatically escalates cyber risk, turning internal blind spots into exploitable attack vectors. Relying solely on centralized Identity and Access Management (IAM) systems to satisfy regulatory requirements creates a dangerous illusion of security and control.
Undermining Regulatory Compliance
Major regulatory frameworks explicitly mandate strict controls over user access, data protection, and auditability. Identity Dark Matter compromises these requirements because unmanaged identities and access pathways provide no verifiable audit trail and cannot be governed by centralized policy.
SOX (Sarbanes-Oxley Act): Requirements for Segregation of Duties (SoD) and access controls over financial systems are bypassed when unmanaged local admin or service accounts grant unauthorized access to these systems. This also removes any auditable record of critical system changes.
PCI DSS (Payment Card Industry Data Security Standard): The need to restrict access to cardholder data on a need-to-know basis and enforce unique IDs is violated when orphaned non-human identities (like API keys) with access to the Cardholder Data Environment (CDE) are left unmonitored and unrotated.
GDPR (General Data Protection Regulation): The principle of ‘least privilege’ for access to Personal Data (PD) is ignored when App-Specifi
The Escalation of Cyber Risk
Identity Dark Matter is the preferred entry point for modern threat actors because it offers a “silent” path to privilege escalation and lateral movement. It serves as the fuel for sophisticated, post-exploitation campaigns that easily bypass traditional perimeter defenses.
Major Threat Campaigns Exploiting Weak Identity:
Successful, high-profile breaches often trace their roots not to a failure of a perimeter firewall, but to the compromise of an identity artifact that resided outside of central governance.
-
Ransomware Campaigns (2024-2025): Modern ransomware groups (e.g., Scattered Spider, Scattered Lapsus$, LockBit, Cl0p) frequently exploit compromised, unmanaged service accounts or local administrator credentials, of improperly guarded CxO accounts for lateral movement or use of deepfake and credential use after initial network access. By compromising an identity outside the central IdP’s scope, they escalate privileges and deploy ransomware or access data without triggering expected identity-based alerts.
-
UnitedHealth Group/Change Healthcare Cyberattack (2024): A major cyberattack targeting Change Healthcare, a subsidiary of UnitedHealth Group, disrupted healthcare operations across the US. Initial reports suggest the attackers gained access through a server that did not have multi-factor authentication, exploiting a lack of security controls around a privileged identity to gain a foothold in the network. This highlights the ongoing danger of unmanaged and poorly secured identities, even in critical infrastructure.
-
The SolarWinds Attack(2019-2020): This landmark compromise highlighted the extreme danger of unmanaged non-human identities. While the initial breach was supply chain-related, the attackers achieved long-term persistence and widespread data access by exploiting poorly monitored API keys and service accounts that escaped standard security scrutiny.
Identity Dark Matter is not merely a policy gap; it represents a security debt that sophisticated attackers are actively leveraging. By focusing on the gaps between systems, threat actors ensure their operations remain invisible to traditional IAM monitoring, leading to longer dwell times and more destructive security outcomes.
By finding and compromising the Identity Dark Matter, attackers gain the ability to move laterally, escalate privileges, and maintain persistence within the network, completely bypassing the robust security perimeter established around the primary, well-managed identities, systems and processes. The successful defense of an enterprise now hinges on identifying, governing, and eliminating this Identity Dark Matter and addressing the unmanaged access footprint.
A better methodology, which also incorporates host-level observability of identity flows, with LLM analysis agentics and AI based evaluation, expands IAM lifecycle management to specifically include unmanaged access artifacts. It proposes a move toward standards-forward adoption centered around standards such as (OAuth, FIDO2) identity postures via a unified control plane with key visibility in the runtime environment.
Further Defining Identity Dark Matter
Patterns of Identity Dark Matter
Our comprehensive research into real-world enterprise environments and attack patterns has allowed us to distill these diverse risks into a framework of “Identity Dark Matter” patterns.
To defend against these threats, CISO’s must first categorize them. Our research identifies a litany of major “Dark Matter” patterns that exist in most enterprises. To effectively defend against the evolving and sophisticated threat landscape, a fundamental shift in perspective is required. We must move beyond simply reacting to known attacks and proactively identify, categorize, and mitigate these hidden security risks that reside deep within our enterprise environments. These obscured security gaps represent the unmanaged, untracked, and often unknown components of an organization’s digital footprint, which we’ve collectively termed Identity Dark Matter.
Identity Dark Matter acts as an increasingly potent attack surface, exploited by adversaries to gain persistence, escalate privileges, and ultimately achieve their objectives.These patterns represent pervasive security blind spots and misconfigurations that are present in most large organizations and serve as critical entry and lateral movement points for threats.
Instead of assuming apps and services are compliant because “they’re supposed to be”, IAM teams must:
-
Observe actual accounts, identity flows and usage at the host or workload level.
-
Infer and actively discover how identity is really implemented and enforced.
-
Compare reality with intended policy.
-
Continuously surface and prioritize deviations.
-
Understand and improve true identity security posture.
Should I just adopt an “EDR for Identity”?
Rather than simply adopting the concept of an “EDR for Identity,” which is would likely be more narrowly interpreted as implying a purely reactive, endpoint-focused solution for monitoring identity activity on devices, we propose a much more comprehensive and architecturally significant approach which evolves to developing and adopting an Identity Control Plane that spans various identity and context sources, code analysis, telemetry visibility and identity context derived by and augmented with an Identity-Aware runtime capabilities (often agent-based) with telemetry to catalog applications and their specific identity control and enhance enterprise capability to provide comprehensive visibility and control. This concept is often called context awareness, which can be applied to remediation efforts and provide better aligned remediation ticketing that helps guide practitioners.
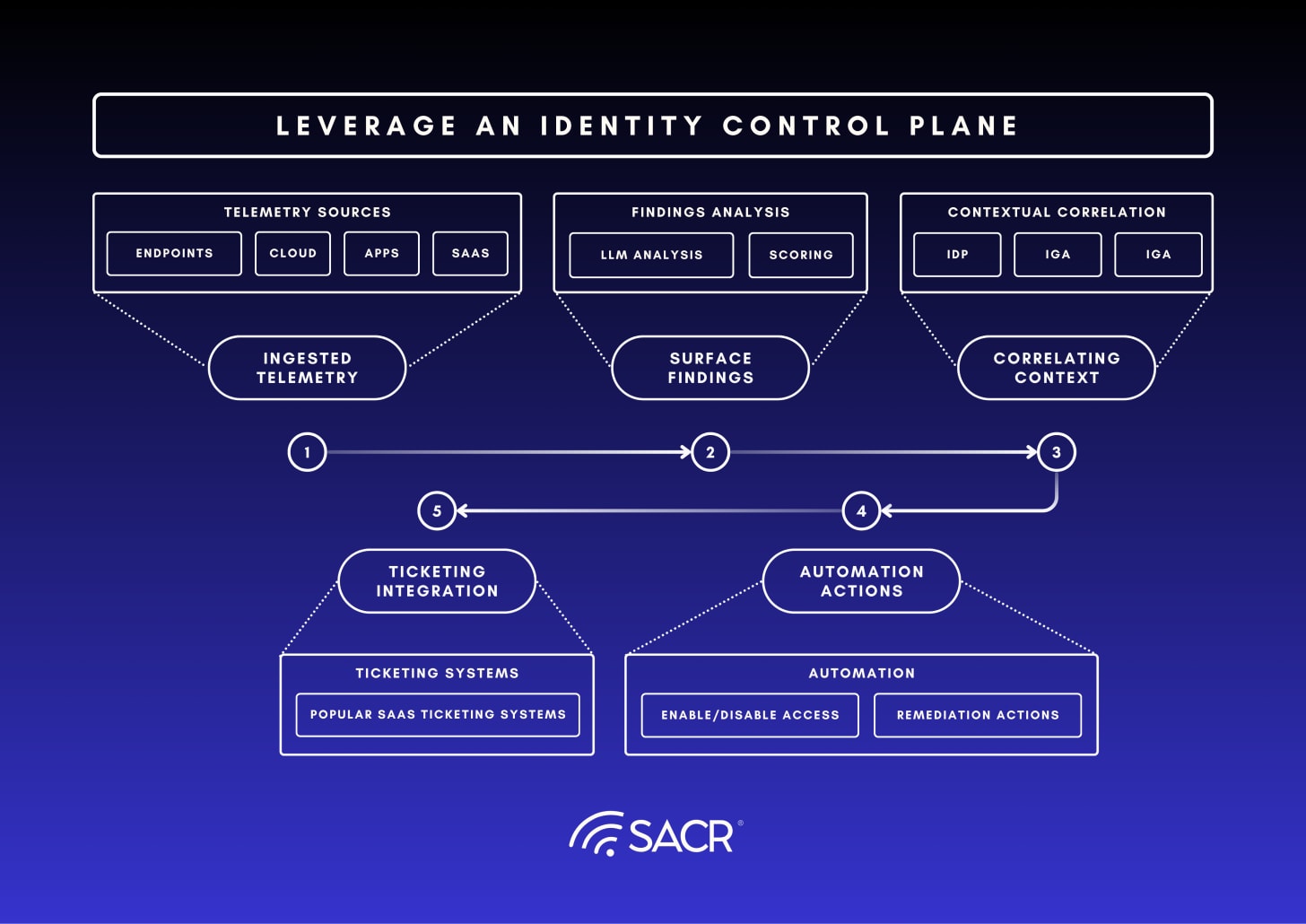
Shine a Light on Identity Dark Matter: Leverage an Identity Control Plane
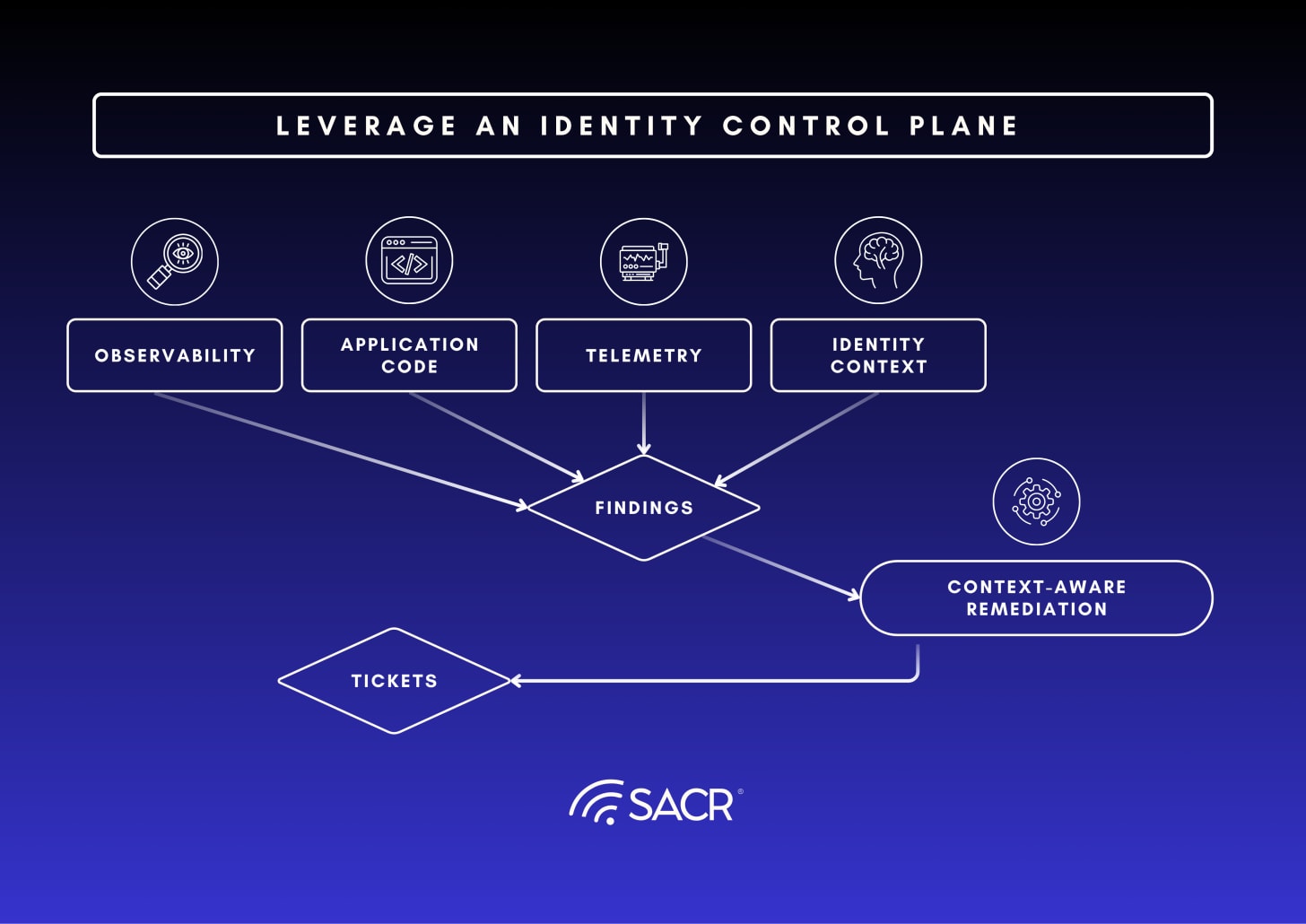
How the Control Plane Functions:
-
Observability: Applying observability before taking action, to understand the flows and potential ramifications.
-
Ingesting Telemetry: Collecting raw authentication and access events (telemetry) from, code reviews, application logs, directory audits, and infrastructure access points (the “seams” between systems).
-
Correlating Context: Tying this raw telemetry to the definitive identity context sourced from the central IdP or IGA system (e.g., Okta, Entra ID, SailPoint, etc). This correlation allows the Control Plane to determine who or what accessed a resource, how they authenticated (e.g., NTLM vs. Kerberos), and if the access aligns with an intended policy.
-
Surfacing Findings: Applying LLM analysis and observability tools to the correlated data to identify discrepancies (risky fallbacks, unrotated tokens, policy bypasses, unknown identity artifacts and runtime connectivity).
-
Enabling Action: Surfacing these discrepancies as audit-ready findings and automating the creation of tickets (in systems like ServiceNow) for remediation, effectively closing the loop from detection to corrective action.
An Identity Control Plane represents a fundamental shift from traditional, siloed identity monitoring and defense mechanisms (as well as the expedient work-arounds that limit their view). It is envisioned as a unified, centralized, and pervasive visibility and control layer that not only monitors but also, with context, actively governs, enforces policy across, and coordinates identity-related security actions for the entire digital infrastructure; including endpoints, cloud environments, applications, services, and privileged access systems. Envisioned as a unified, centralized, and pervasive layer that actively governs, enforces policy across, and coordinates identity-related security visibility along with actions across:
-
Endpoints
-
Cloud environments
-
Applications
-
Services
-
Privileged access systems
Its purpose is to act as the authoritative decision-making and enforcement nexus for all identity lifecycle and access events throughout the organization.
The Identity Control Plane acts as the authoritative identity discovery, decision-making, remediation and enforcement nexus for all identity lifecycle and access events. It moves beyond passive detection to provide real-time context, risk scoring, and automated remediation, making it the essential backbone for proactive identity defense against advanced threats like lateral movement and credential abuse, ensuring real world Zero Trust3 principles are dynamically and consistently applied everywhere various identities are used. This new architecture sits above the existing infrastructure, acting as a correlation engine to deliver rich visibility, control and orchestration.
Technology Impact
Update your Assessment Methodology: Move them From Unknowns to Knowns
How does an organization assess its Identity Dark Matter mass? We propose an evidence-based, tool-agnostic checklist:
-
Where to Instrument: Focus on the “seams” between systems and from within code, application logs, traffic flows, directory audits, and cloud infrastructure access logs.
-
Signals to Collect: Look for authentication in code and various events utilizing non-standard protocols (e.g., NTLM vs. Kerberos), logins from accounts and SaaS connections not present in the IdP, and privilege escalation events or management systems.
-
Triaging Risk: Classify findings by criticality. A local admin account is a “High” risk; a partial SSO adoption for a non-critical app might be “Medium.”
Operational Approach: Connect or Collapse
An “Identity Control Plane” uses a “Connect and Collapse” style approach as its core strategy to address the fragmented nature of modern identity management. This strategic framework aims to establish a unified, actionable Zero Trust security posture by consolidating disparate identity silos. The simple, two-pronged “Connect and Collapse” method achieves this by integrating a wide range of platforms from cloud environments like AWS to on-premises directories such as Active Directory, and Identity Providers like Okta along with endpoint telemetry. This consolidation moves beyond mere visibility to become a necessary step for achieving practical identity security and control.
-
Connect: Review code with automation and ingest data from existing silos (Okta, Active Directory, AWS) to create a unified view.
-
Collapse: Where possible, retire shadow directories and force federation.
-
Result: This leads to a Zero Trust posture that is actionable, not just theoretical.
-
Repeat: Close the loop by repeating these steps on a regular basis.
Challenges and Buyer Guidance
Dark Matter Challenges:
-
The primary obstacle is political, uncovering “Identity Dark Matter” often reveals process failures in IT or Engineering. Unmanaged, untracked, and often forgotten identities, permissions, and service accounts often involve political rather than technical challenges such as ownership, independence and proper executive sponsorship as well as program alignment to these potential risks and gaps.
-
Identifying and remediating this “Identity Dark Matter” inherently exposes process failures, oversight gaps, or poor communication within IT Operations, Engineering, or even line-of-business application teams.
-
When an investigation reveals that a high-privilege account has been provisioned and forgotten, or that a development service account retains excessive permissions long after a project has concluded, it necessitates uncomfortable accountability. This resistance can manifest as defensive posturing, the minimization of risk, or outright denial, making it challenging to gain the cross-functional support and resources required for a comprehensive Identity Dark Matter clean-up initiative.
-
Overcoming political friction and securing executive buy-in and establishing a blame-free mandate for process improvement is often the first and most critical hurdle in strengthening the overall identity defense posture.
CISO Guidance
Core Evaluation Criteria (The Must-Haves)
To effectively address the challenges posed by Identity Dark Matter and shore up identity defenses, any solution must meet a set of fundamental requirements. The following criteria represent the non-negotiable capabilities essential for a comprehensive and proactive identity security strategy.
-
Expanding the breadth of Discovery: Look beyond the managed identity you can see in your current stack and find the unmanaged dark matter that lives outside.
-
Telemetry: Does this tool require an agent on every server, or can it ingest existing logs and observability telemetry to minimize deployment overhead?
-
Policy Bypass: Can it detect and surface access that bypasses the primary SSO or IdP, or is it limited to only analyzing IdP-mediated logs?
-
Effective Audit Reporting: Does it support “Audit-Ready by Default” reporting, providing a single, verifiable source of truth for effective access?
Key Integration Priorities
To effectively combat the pervasive challenge of Identity Dark Matter and strengthen overall identity defense, organizations must focus on several critical integration priorities. These integrations are essential for unifying disparate identity and security data, enabling continuous monitoring, and automating response capabilities across the entire digital ecosystem.
-
Does the solution integrate with adjacent compliance evidence systems (Drata)?
-
Does the solution integrate with adjacent Endpoint tools for greater visibility (Duo, Crowdstrike, Microsoft Defender, others)?
-
Does the solution provide out-of-the-box connectors to your primary identity systems (Entra ID, Okta, Active Directory)?
-
Can it integrate with your IGA platforms (SailPoint, Saviynt) to add context on entitlements and de-provisioning status?
-
Does it natively link findings to your ticketing system (ServiceNow, Jira) for automated remediation workflow creation?
Potential Red Flags:
The presence of Identity Dark Matter often manifests in several observable ways within an organization’s identity infrastructure, serving as clear indicators that critical security blind spots exist. Recognizing these potential red flags is the first step toward mitigating the risk posed by unmanaged and unknown identities and access permissions.
-
Requires “Rip and Replace”: Any vendor that demands a complete replacement of your core IdP or IGA system to gain initial visibility.
-
No “Connect or Collapse”: A solution that cannot ingest data from multiple, siloed directories and instead requires forcing all identities into a single, new store.
Conclusion and Recommendations
Key Findings Summary
-
Identity security is failing not at the policy level, but at the implementation level (Identity Dark Matter).
-
Attackers exploit the gaps between systems and unseen or unmanaged elements of identity (fallback paths, local accounts, shadow IT, application drift, legacy remnants and more).
-
Dashboards are insufficient; a unified Control Plane is required.
Identity security is currently hampered not by the lack of well-defined policies, but by critical failures at the implementation level, a phenomenon we’ve termed “Dark Matter.”
The Dark Matter represents the often-overlooked gaps. These hidden elements operate outside the purview of standard identity and access management (IAM) tools and security team visibility, rendering them effectively invisible to security teams. This creates vast, unmonitored attack surfaces that sophisticated adversaries actively exploit.
Current defensive strategies, often relying on static dashboards and siloed tools, are inadequate for combating this issue. A truly effective defense requires moving beyond mere visibility to establish a unified Identity Control Plane. This central plane must integrate security controls, governance, and enforcement across all identity systems, bridging the “Dark Matter” gaps that attackers currently leverage. By unifying control rather than just aggregating data, organizations can eliminate the exploitable weaknesses at the seams of their identity infrastructure, transitioning from a reactive, gap-filled security posture to a proactive, comprehensive one.
Actionable Recommendations
To effectively combat Identity Dark Matter and enhance your overall identity defense posture, security and IT teams must implement a strategic set of actions. The following recommendations provide a practical framework for identifying, mitigating, and proactively preventing the security risks associated with unmanaged and forgotten identities and permissions.
Phase 1
Discovery: deploy a “Visibility First” pilot. Do not block access; simply instrument critical applications to detect bypass attempts and local account usage. Prefer runtime visibility to accelerate discovery and completeness.
Phase 2
Sanitization: Systematically eliminate NTLM fallbacks and vault/rotate orphaned service account credentials. Prefer solutions that help create a complete visibility and control, and helps apply zero trust identity principles.
Phase 3
Unification: Route all authenticated traffic through the Identity Control Plane to enforce continuous evaluation. Ensure that you action discovery phases to address and mitigate gaps and remediate the Identity Dark Matter problem.
Phase 4
Control: Move from reactive remediation to a proactive, continuous control posture by leveraging the Identity Control Plane as the central enforcement point. This phase establishes persistent, dynamic security and governance over all identities, managed and unmanaged.
Future Outlook
The Rising Threat of Identity Dark Matter
Within the foreseeable future and over the next three to five years a critical, often disregarded security concern Identity Dark Matter is projected to solidify its position as the principal target for increasingly sophisticated and destructive ransomware attacks. Identity Dark Matter is believed to already be an extensive, unmanaged, and often neglected aspect of digital identities, entitlements, credentials, and access vectors that reside outside the protective scope of an organization’s centralized Identity Provider (IdP) or Identity and Access Management (IAM) solutions.
Enterprises that do not achieve comprehensive, continuous visibility and control over these digital blind spots will retain a fundamental state of continuous vulnerability. Substantial investment in a leading IdP solution is no longer a sufficient protective measure; the security efficacy of the IdP is instantly neutralized should a threat actor exploit an unmonitored path to gain initial access, execute lateral movement, and elevate privileges utilizing an identity never registered or governed by the central IdP. This foundational visibility constitutes the sole sustainable defense mechanism against ransomware and other advanced persistent threats specializing in identity-based lateral movement and privilege escalation. The future of identity defense resides in illuminating and governing the Dark Matter before it serves as the launching point for the subsequent major security breach.
Vendor Profile
Orchid Security
Orchid Security provides an identity security control plane that enhances identity defense helping its users identify Identity Dark Matter as defined in our research article. It functions by discovering how applications implement identity, identifying insecure fallback paths and policy gaps, and helping centralize enforcement. Its enforcement capability operates above existing Identity Provider (IDP), Identity Governance and Administration (IGA), and app-level controls. Orchid Security offers capabilities to discover all applications running on any visible host and automatically assess the authentication and authorization flows used by each application. Effectively reducing the problem space faced by the emergence of Identity Dark Matter.
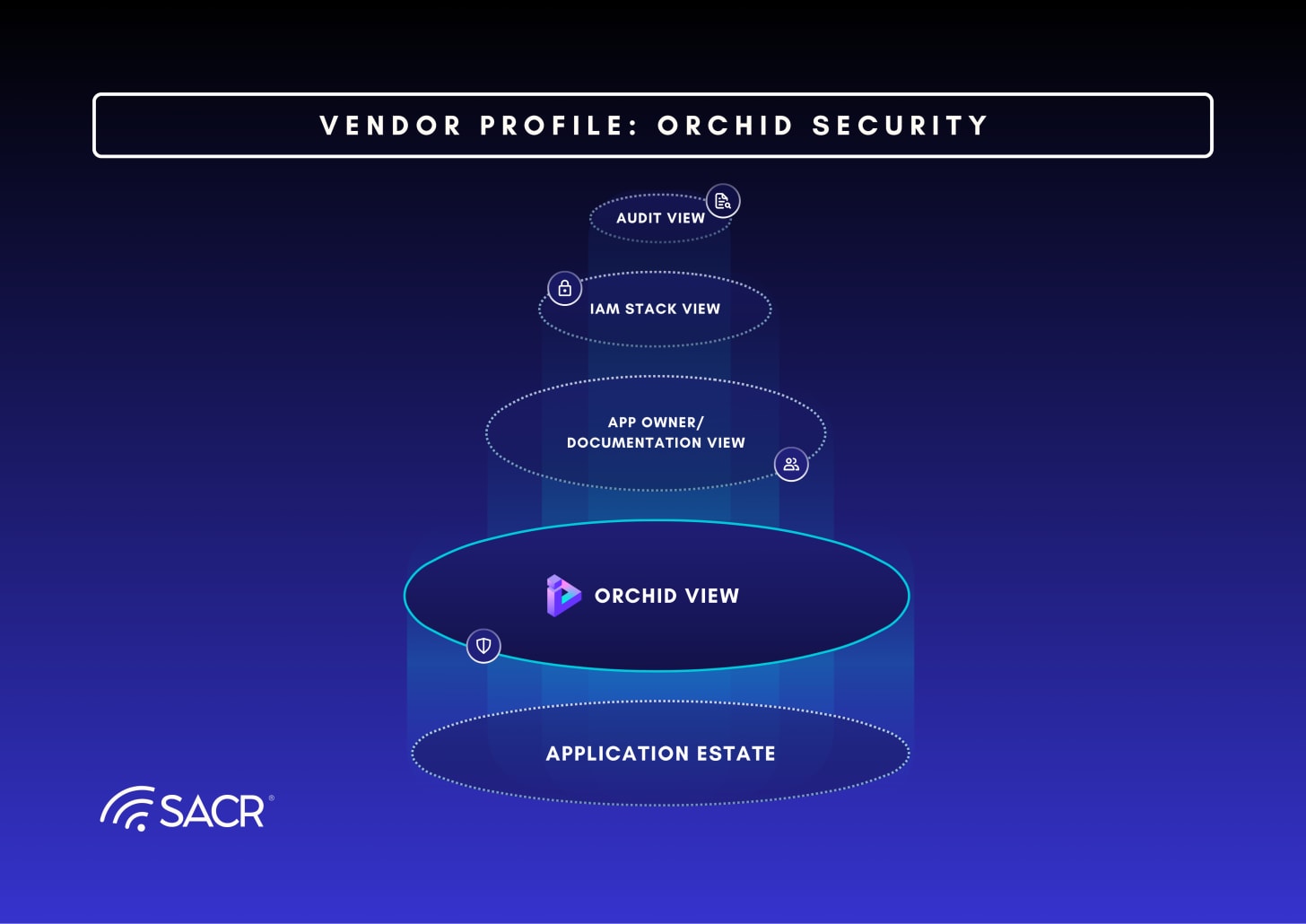
The core concept Orchid Security uses is to widen the visibility across the Identity and Runtime stacks – well beyond the IAM stack. Below is an architectural representation that Orchid uses to illustrate this concept. We agree with this expanded view.
Core Capabilities
-
Agent-based, host-level observability of identity flows using OpenTelemetry with LLM-assisted analysis.
-
Detection of alternative or insecure authentication paths such as NTLM fallbacks, long‑lived tokens, and non‑MFA routes.
-
Mapping of authentication methods, privileges, and app-coded behaviors to reveal where central controls are not enforced.
How Orchid Addresses the Dark Matter Gap
-
Visibility First: Orchid does not require “rip and replace.” It begins by illuminating the Dark Matter, providing immediate value through visibility before exposure remediation begins. It offers a host discovery service to discover and identify identity applications.
-
Contextual Intelligence: By tying raw telemetry to identity context, Orchid distinguishes between legitimate behavior (a service account running a scheduled task) and anomalies (that same account logging in interactively). Orchid achieves this through a host-level agent that feeds observability telemetry into an analytical layer, using LLM analysis and prompt engineering to accurately map identity flows and surface hidden risks.
-
Standards-Forward: Native support for OAuth, OIDC, and FIDO2 ensures that as you remediate, you are moving toward a modern, passwordless future.
Integrations and Ecosystem
-
Microsoft Entra (Identity)
-
SailPoint (Identity)
-
ServiceNow (for ticketing workflows)
-
CrowdStrike (Context)
-
SentinelOne (Context)
-
Okta (Identity)
-
Active Directory (context)
-
Ping Identity (Identity)
Business Value
-
Orchid Security claims to offer shortened application onboarding (from weeks to days) by automating extraction of IAM controls and policy mapping.
-
Orchid Security claims to reduce professional services costs and improve audit and compliance posture with a focus on real‑time insights.
-
Orchid claims to improve cyber security and compliance posture, by proactively uncovering exposure and remediating much of it without extensive effort or re-coding.
Deployment and Operations
-
Orchid claims to offer a low‑friction rollout capability with minimal footprint, no kernel hooks or admin mode, which is ideal and avoids challenges that exist in driver-oriented agent solutions.
-
Deploying Orchid security follows a standard procedure involving starting with a Proof of Concept (PoC) in a test environment, followed by scaling the deployment using the AWS Marketplace and existing device management tools (such as Intune).
Risks and Considerations
The successful implementation of new identity defense mechanisms is as critical as the technology itself. CISO’s should evaluate the necessary considerations, potential pitfalls, and strategic approaches before adopting and during the deployment phases to ensure maximum effectiveness, minimize disruption, and build a robust, sustainable operational foundation for identity security. Several key factors must be considered during the implementation phase to ensure maximum effectiveness and a smooth transition.
Implementation Considerations and Challenges
-
Successfully deploying any new security solution, including advanced identity defense mechanisms, requires careful planning and execution.
Initial Configuration and Environmental Alignment
-
Initial setup of identity defense tools is complex and resource-intensive, demanding deep technical expertise. Optimal alignment with a heterogeneous enterprise environment is critical; a ‘set-and-forget’ method fails. The team must accurately map the organization’s unique identity landscape, including legacy systems and diverse policies, to the tool’s capabilities. Misconfiguration risks security gaps, excessive false positives, or business disruption. This phase is essential for a strong operational foundation.
Integration Breadth, Depth, and Deployment Effectiveness
-
The success of identity defense tools hinges on seamless integration across the entire technology stack, including standard directories (Active Directory, Azure AD) and a growing ecosystem of applications, cloud services, SIEMs, and orchestration platforms. Organizations must evaluate the breadth and depth of application integrations offered. Insufficient application coverage (or “rollout breadth”) leaves parts of the identity attack surface unprotected, compromising the overall security posture and undermining the tool’s investment.
Phased Rollout for Complex and Heterogeneous Estates
-
In complex, heterogeneous IT environments, a rapid, full-scale deployment is always potentially risky. A carefully managed phased rollout, especially of agent based technology is strongly recommended. This incremental approach starts with a small pilot or specific business unit to test configuration, validate integrations, and refine procedures. This iterative process minimizes service disruption, allows for early conflict remediation, and builds organizational confidence before scaling enterprise-wide.
Conclusions
It is imperative that contemporary enterprise security mandates transition toward audit-ready, Zero Trust posture Dark Matter-aware solutions where holistic visibility and governance is established as a non-negotiable baseline and standard. Attaining this state requires a paradigm shift, strictly mandating that no identity whether human, machine, AI agent, or service should be permitted to operate without scrutiny. Every credential and access right must be continuously discovered, inventoried, monitored, and controlled with an Identity Control Plane.
**************
Reference Citations