Actionable Summary
- It’s been over three months since Palo Alto Networks announced its acquisition of CyberArk, a move that drew widespread attention across the cybersecurity industry. Numerous analysts have since offered detailed perspectives on the transaction, such as “The Case For and Against Palo Alto Networks Acquiring CyberArk. The deal itself is historic. For many PANW observers, this represents a departure from Palo Alto Networks’ traditional focus on smaller, incremental acquisitions.
- This report does not aim to introduce new commentary, but rather to address several questions that still remain open: What does this acquisition reveal about the current state of security platforms? How does identity fit into Palo Alto’s broader strategy? And more importantly, what does this mean for the future of identity security and the PAM market?
- In our view, this merger signals a potential shift in how identity security platforms are integrated and delivered. It raises an important question for Chief Information Security Officers (CISOs) and practitioners: will organizations consolidate their security investments under a single vendor, or will they continue to favor a best-of-breed approach? If Palo Alto Networks succeeds, it could reinforce the appeal of unified security ecosystems. If not, it may strengthen the case for maintaining diverse vendor portfolios (which won’t be surprising).
- The Privileged Access Management (PAM) market is going to evolve significantly as a result of this acquisition. For newbies, PAM has historically focused on identifying all privileged identities, and controlling and enforcing their access through lifecycle controls and time-bound policies. Every privileged action is monitored and audited, with tools capable of detecting, alerting, or even terminating risky sessions in real-time. Now, with AI agents, this problem has multiplied even more for enterprises. How will PANW manage CyberArk to take on this market?
- Finally, this report provides an in-depth analysis of both companies’ strengths, the evolution of PAM, CyberArk’s expansion into new identity domains, and the broader implications of this merger for the enterprise security industry.
Thanks for reading Software Analyst Cyber Research! Subscribe for free to receive new in-depth reports and cybersecurity analysis.
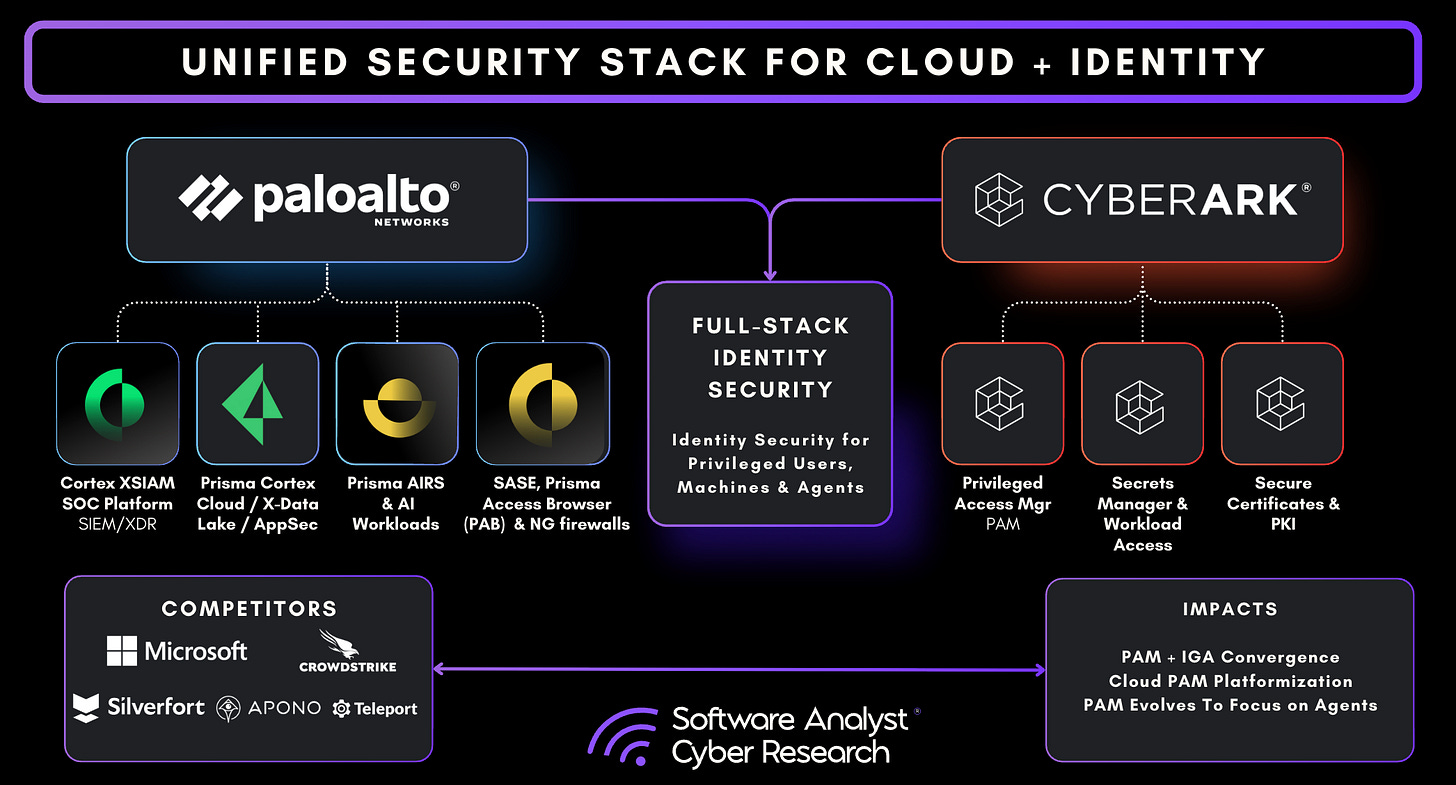
Why Palo Alto Networks Made the Acquisition?
Palo Alto Networks has long been recognized as a cybersecurity powerhouse with one of the most comprehensive cybersecurity portfolios that spans network, cloud, and security operations. Its capabilities are broader than those of CrowdStrike and positioned just behind Microsoft in terms of scope and integration. Understanding the rationale behind the CyberArk acquisition requires examining the core pillars of the Palo Alto platform today (pre-CyberArk).
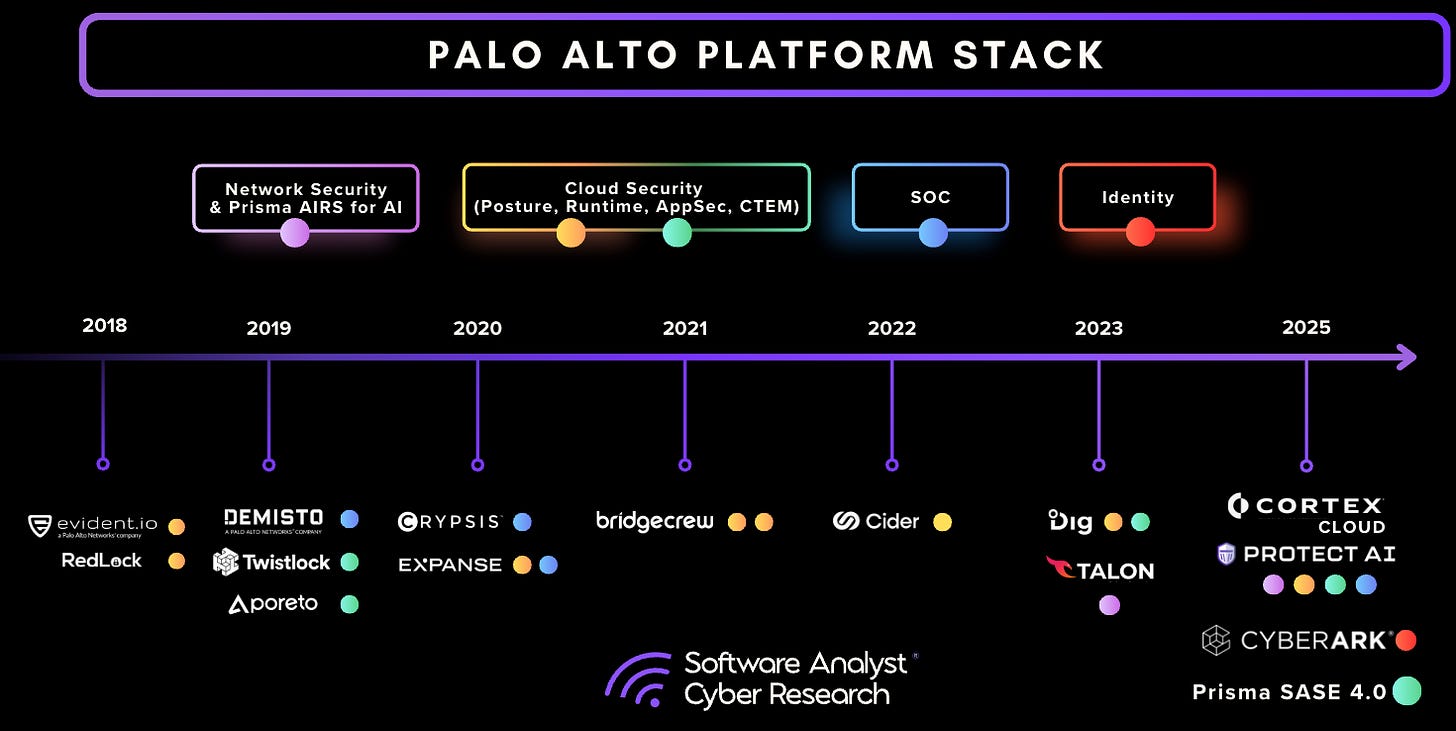
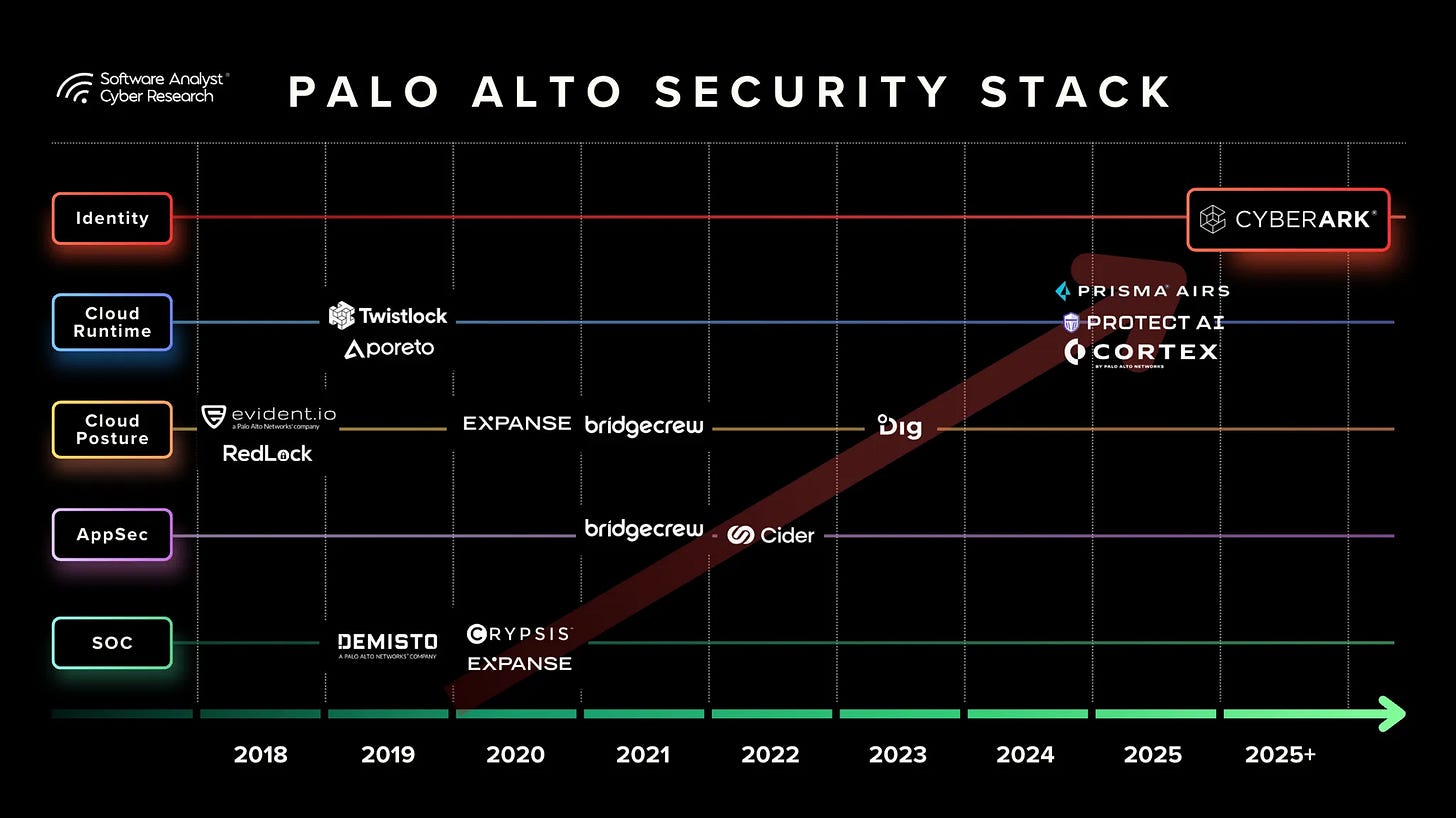
Network security has always been the foundation of Palo Alto Networks’ business. This includes several key offerings:
- Firewall security, the company’s traditional stronghold.
- The Secure Access Service Edge (SASE) platform, delivering unified network and security
- Prisma Access Browser (PAB), extending secure access capabilities to the endpoint
- Prisma AI-driven capabilities (Prisma AIRs), which they have already incorporated across many of their AI Security platforms
These components established Palo Alto’s leadership in securing network and perimeter environments while laying the groundwork for further platform expansion. This strong foundation enabled the company to build its second major pillar: a robust cloud and security operations portfolio.
The Second Pillar: Cloud and Security Operations
Building on its network security foundation, Palo Alto Networks launched Cortex Cloud, which we covered in a previous report, marking a significant evolution in its platform strategy. Cortex represented one of the most extensive integrations of cloud and security operations (SecOps) capabilities in the industry, combining proactive and reactive defenses.
Core capabilities included:
- Cloud security,
- Application security,
- SOC transformation,
- Endpoint protection,
- Exposure management,
- Automated remediation, and
- Basic threat detection for email security
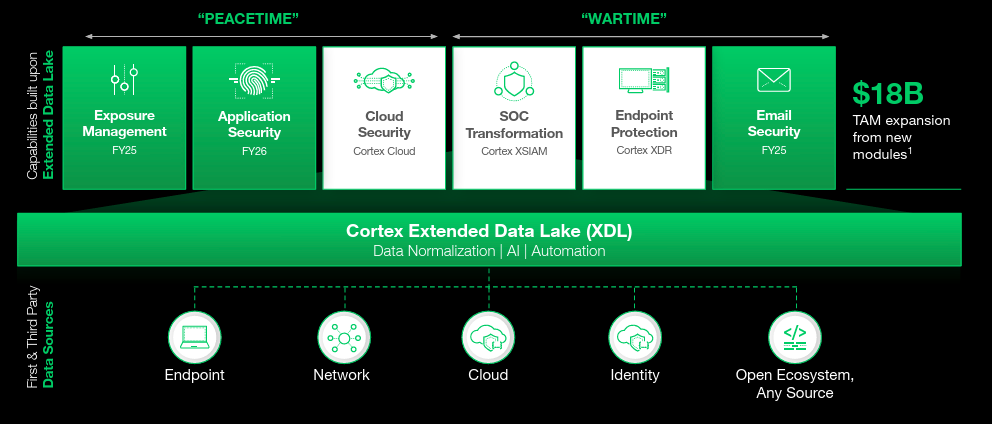
These capabilities enabled organizations to consolidate risk visibility across network, endpoint, and cloud environments, while also automating threat response at scale. Cortex was a direct response to the increasingly complex and fast-moving threat landscape, as well as to competitors expanding their own SecOps offerings.
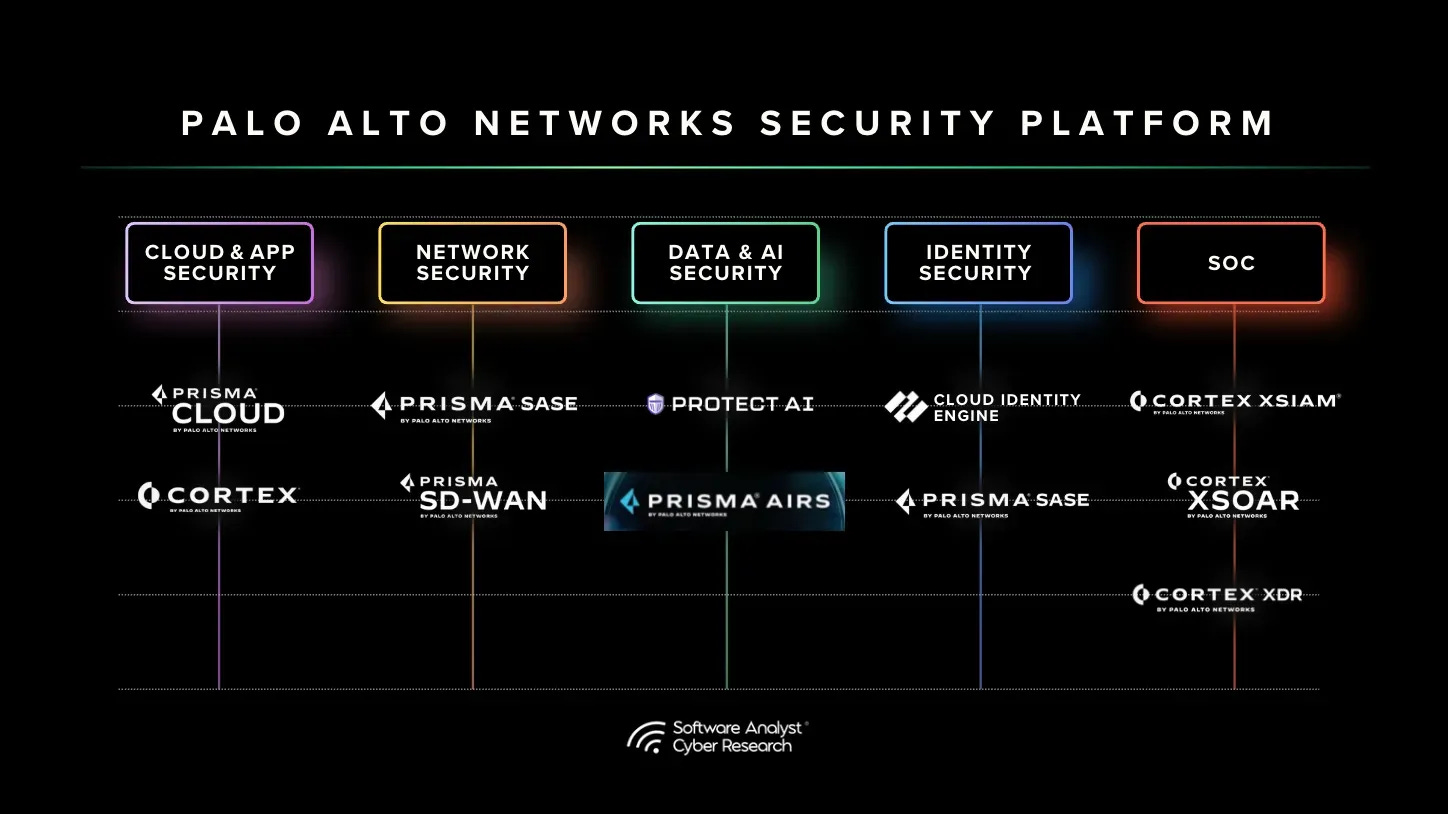
Together, these domains gave Palo Alto breadth across infrastructure and operations. Yet breadth is not the same as completeness. Even with Cortex, Palo Alto still lacked a critical dimension – identity security. Network and cloud defenses, no matter how advanced, cannot fully protect an organization if privileged accounts remain exposed. CISOs have long understood that the most significant vulnerabilities often lie not in infrastructure, but in the administrator credentials that grant unrestricted access to it once compromised. For Palo Alto, addressing identity security was essential to completing its platform vision. CyberArk, with its leadership in PAM and identity security, represented the logical, if somewhat unexpected, solution.
Identity Becoming The New Perimeter
At Software Analyst, we believe that identity has become the new perimeter in modern cybersecurity. As the traditional network edge continues to dissolve, identity will define the next generation of security architecture, and with it, the most significant opportunities for innovation and differentiation.
The legacy model of network-based security is increasingly inadequate in a world defined by SaaS adoption, hybrid and multi-cloud infrastructure, distributed workforces, and the rise of agentic and machine-to-machine access. In these environments, the boundaries that once defined enterprise networks no longer exist in a fixed, predictable way.
The decisive control point has therefore shifted. The authoritative answer to the question, “Should this request be allowed?” now resides not in network subnets or firewalls, but in identity systems i.e. the mechanisms that understand who or what is making a request, under what conditions, and with what entitlements. This transition reframes security around trust, verification, and contextual access rather than static boundaries.
Why CyberArk
CyberArk is a cybersecurity company that specialized in protecting the most powerful accounts and credentials within an organization, such as administrator, root, and service accounts. These identities represent the most powerful access points within an organization. If compromised, they can provide attackers with unrestricted control over critical systems and data. At its core, CyberArk delivers a secure vault for storing and managing sensitive passwords and secrets, along with tools to strictly control who can use them, when, and for what purpose. The platform determines who can access privileged credentials, when they can be used, and for what purpose. It continuously monitors and records privileged sessions, applies just-in-time (JIT) and least-privilege principles, and dynamically adjusts permissions based on contextual risk. This ensures that sensitive assets across servers, cloud environments, and business applications remain protected from misuse, insider threats, or cyberattacks. In simple terms, CyberArk acts as the guardian of an organization’s most sensitive access, its “keys to the kingdom.”
CyberArk’s dominance in PAM
CyberArk enters this merger, as quite frankly, the undisputed leader in Privileged Access Management (PAM). Its leadership is built on robust capabilities and competencies across PAM controls, JIT ephemeral access, secrets management for cloud and Kubernetes environments, and fine-grained zero trust authorization. But this leadership didn’t emerge by chance. It is the outcome of a focused, deliberate strategy that has evolved over more than two decades.
First-Mover Advantage & Focus
Since its founding in the late 1990s, CyberArk focused almost exclusively on privileged accounts i.e. administrator accounts, service accounts, and root credentials that represented the highest-value targets for attackers. While many competitors diversified into broader identity or security portfolios, CyberArk concentrated on developing deep expertise in vaulting, session isolation, and credential lifecycle management.
That singular focus gave CyberArk a significant first-mover advantage and helped it build unmatched credibility with CISOs who were prioritizing insider threats and compliance needs in the early 2000s. Over time, this credibility translated into market leadership and a reputation for operational rigor and reliability.
CyberArk’s strength lies in its ability to implement comprehensive privilege controls that cut across multiple domains, including:
- Entitlement management
- Session management
- Automated policy enforcement and authentication management
- Credential management
- Automated lifecycle
The company’s core expertise is rooted in its deep ability to provision and enforce privilege controls for technical and administrative roles (Cloud Ops, Engineers, Developers, cloud ops teams, third parties, data scientists, engineers, and developers). These roles often hold credentials with broad and sensitive access to infrastructure, workloads, and SaaS applications. When compromised, such credentials effectively grant attackers the “keys to the kingdom.”
CyberArk has distinguished itself by successfully applying these controls across on-prem and legacy systems that are often the most difficult to secure such as Oracle, SAP, Windows Server, Linux, and SQL Server. These long-lived environments have historically posed some of the toughest identity and privilege management challenges in enterprise IT. CyberArk built its reputation by solving precisely these problems, earning the trust of security and infrastructure leaders across industries.
Building PAM is Hard (Nobody Has Come Close)
CyberArk’s core differentiator has long been its Digital Vault, the foundational component that set it apart from competitors. The Vault was engineered as a hardened, isolated repository for sensitive credentials, designed with advanced encryption, segregation of duties, and tamper-resistant architecture. Few competitors have been able to replicate its level of security assurance or operational resilience.
Over time, CyberArk expanded this foundation by introducing the Privileged Session Manager (PSM) and Privileged Threat Analytics (PTA) modules. Together, these components extended the platform’s reach beyond credential storage into real-time session monitoring and detection capabilities tied directly to privileged activity.
This evolution transformed CyberArk’s offering from a password vault into an end-to-end lifecycle management platform that addressed both regulatory compliance (including SOX, PCI, and HIPAA) and active threat detection. The result was an architecture that organizations could integrate seamlessly into their daily operations, blending security, governance, and operational accountability.
Since the inception of the PAM market, no vendor has successfully matched CyberArk’s combination of security assurance and operational resilience. Despite significant investment across the identity security landscape, CyberArk continues to define the standard that others attempt to reach.
Enterprise-Grade Approach & Ecosystem Positioning
CyberArk built for the Fortune 500 from the beginning. Its architecture was designed to be scalable, resilient, and deeply integrable, supporting seamless connections with Security Information and Event Management (SIEM) systems, ticketing systems, and, more recently, cloud infrastructure and DevOps toolchains. This made the company the “default choice” for highly regulated industries, such as financial services, energy and government, where privileged misuse represented existential risk.
Beyond technology, CyberArk invested heavily in building an ecosystem-driven strategy. The company prioritized partnerships and integrations across the IT and security landscape, ensuring that its platform could operate as a core control within enterprise workflows, rather than as an isolated or standalone product. This ensured CyberArk was never just a tool on the side, but a control woven into enterprise workflows.
Expansions Were A Little Late
While staying rooted in PAM, CyberArk steadily expanded into adjacent areas like Identity Security and Secrets Management (Conjur, acquired in 2017). It’s platform has evolved to address not only human users but also the rapidly growing universe of non-human identities such as workloads, bots, and AI agents that now outnumber human identities by ratios as high as 40:1 in many enterprises.
Over recent years, CyberArk has made significant strides to secure more aspects of the identity security market:
- Authentication, through its acquisition of Adaptive
- IGA solutions, through the acquisition of Zilla Security
- Machine Identity Management, through its acquisition of Venafi
- Identity-as-a-Service (IDaaS: SSO, MFA), adaptive auth, through its acquisition of Idaptive
- Workload Access Solutions by extending zero-trust enforcement to applications, APIs, and automated workloads
CyberArk is providing tools to manage the lifecycle, access, and secrets for millions of machine identities, enabling organizations to apply zero-trust principles even to autonomous agents.
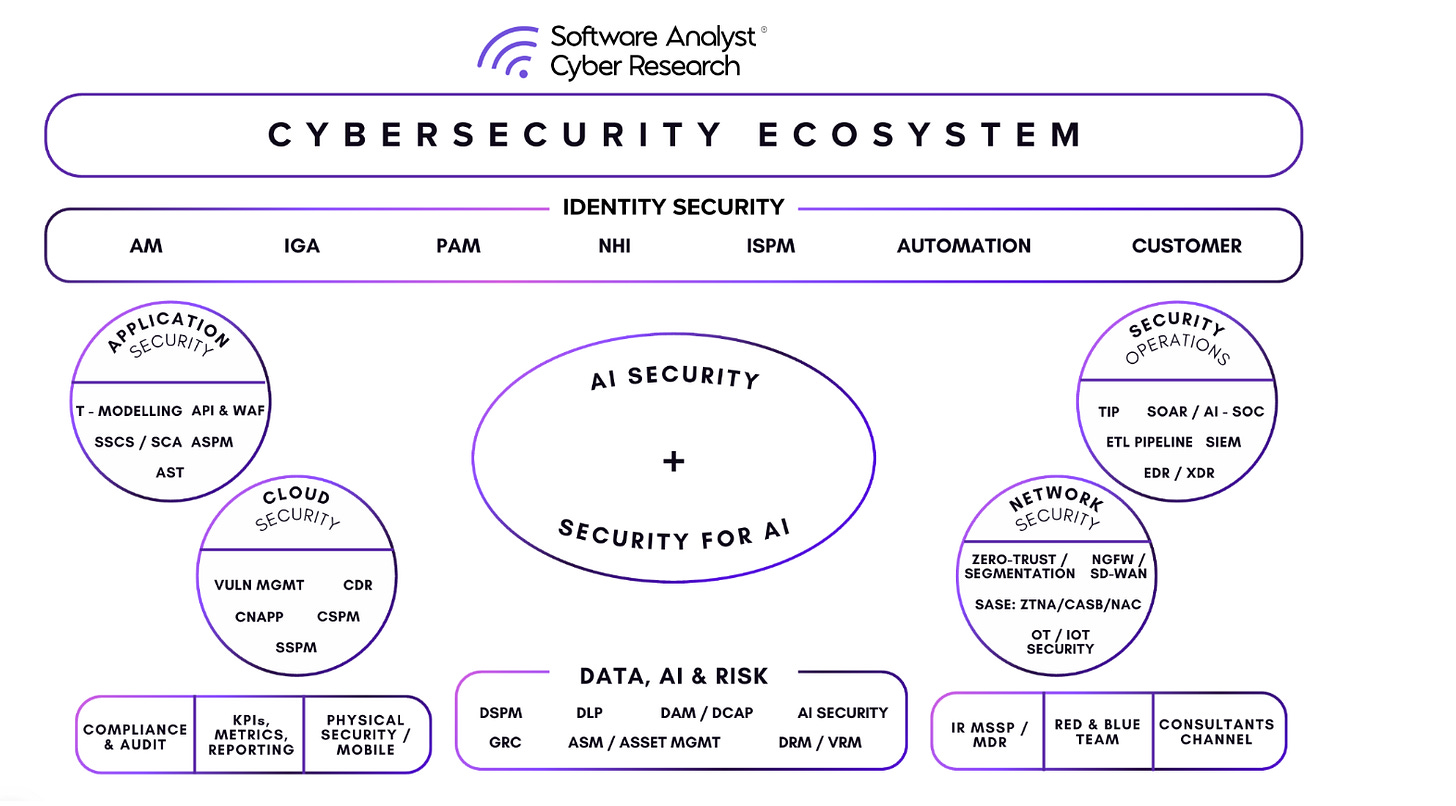
The Opportunities In Identity Security
Now, let’s step back and discuss the future of identity security. The largest identity risks (and opportunities) concentrate where authentication and lifecycle governance fail.
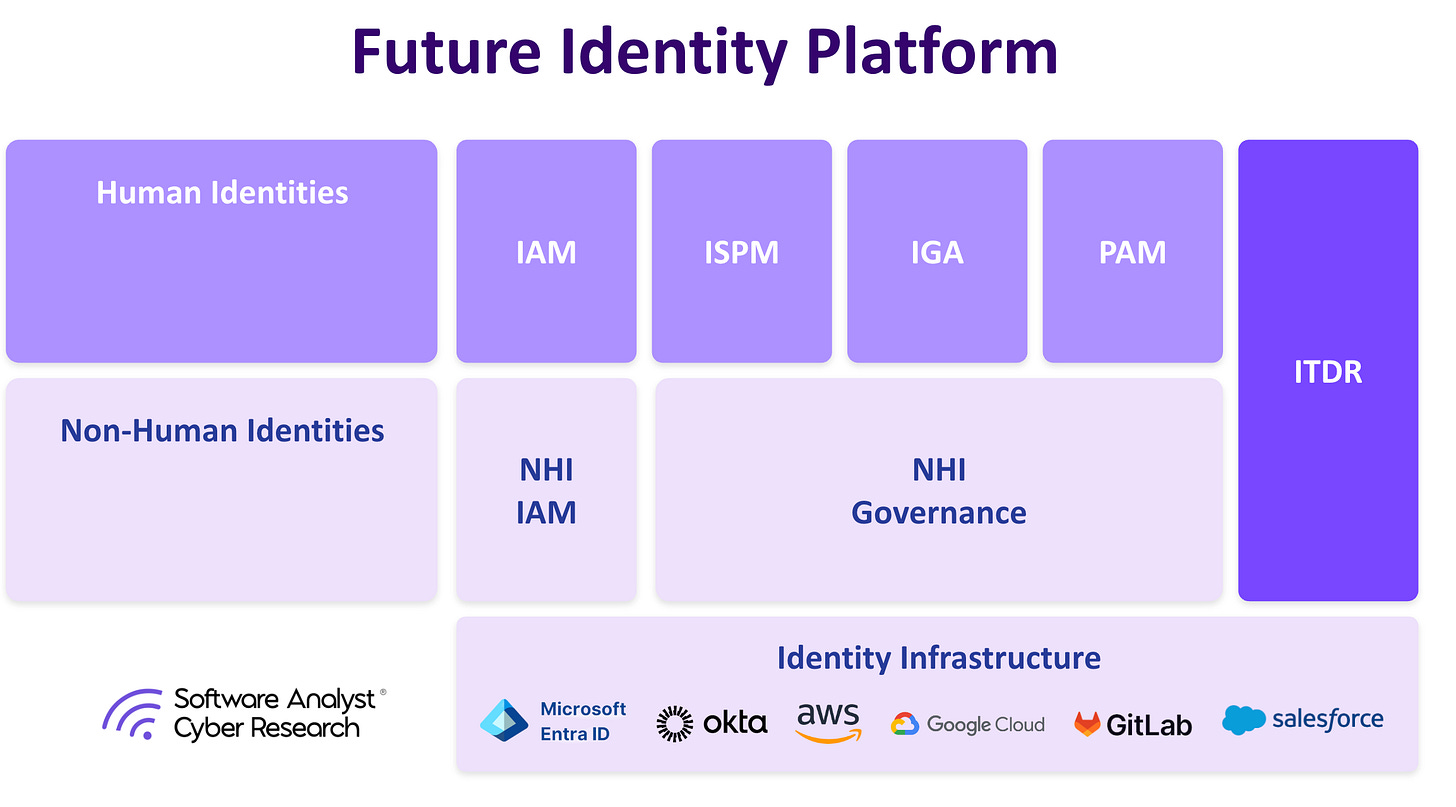
The industry’s next transformation will converge these domains across five foundational pillars:
- IAM (Identity and Access Management): the connective tissue of authentication, SSO, IDP and federation. We’ve mostly this issue for humans, but NHIs require their own specialized for verifying an agent.
- Visibility: ISPM (Identity Security Posture Mgmt). We need a connective tissue that sees ALL identities and gives you enough context. This thrives around visibility, drift detection, and continuous posture assurance for identity configurations. Everyone needs a graph-based architecture to tie in identity across SaaS, cloud and AD.
- IGA (Identity Governance and Administration): the brain for lifecycle orchestration and compliance, increasingly AI-assisted for access reviews and automating many of the compliance-heavy parts of this area. Increasingly, we need to cover the lifecycle of agents, including access controls.
- Non-Human Identity IAM & Governance, built to manage service accounts, machine users, API keys, tokens, and agentic workloads that now outnumber humans in the enterprise.
- PAM (Privileged Access Management): The guardrail for elevated entitlements and just-in-time access will be more important. Most of this issue has been solved on-prem, but we need more for cloud workloads and increasingly for agents.
- ITDR (Identity Threat Detection & Response): Runtime is the next battlefield. No amount of posture will save you. Detection and Response against lateral movement or identity-based attacks is the nervous system that detects and responds to credential misuse and identity-based attacks.
If we go into more depth and uncover most of this deeply, this is how it breaks down for us.
Authentication Layer
While visibility into AI agents and shadow AI presents a major emerging opportunity, the authentication layer remains a more critical and complex challenge facing enterprises today.
On the authentication side, adversary-in-the-middle toolkits and token theft routinely bypass legacy, phishable MFA and weak recovery flows. In parallel, long-lived sessions, inconsistent authentication enforcement across VPNs, command-line interfaces (CLIs), legacy protocols, and remote administrative paths create hidden entry points for identity-based lateral movement. Compounding these risks, poor rate limiting, password reuse, and credential stuffing remain persistent issues that continue to undermine enterprise authentication integrity at scale.
On this front, we like what companies like Astrix and 1Password are doing within this ecosystem.
1Password has evolved beyond its roots in consumer password management to position its platform as an AI Gateway for agent access. Using its vault and browser automation capabilities, 1Password enables AI agents to authenticate to applications and services without directly exposing raw credentials. Client-side autofill and policy-based item sharing ensure that agents receive only the scoped secrets or tokens necessary to complete a given task. The company is also extending its coverage beyond traditional SSO environments to secure non-federated applications, experimenting with client-side versus server-side brokering patterns to reduce exposure. These mechanisms bind sessions to device context and support automatic secret rotation or revocation once an agent’s workflow concludes, minimizing blast radius and improving operational hygiene.
Astrix, meanwhile, is addressing the challenge from the enterprise infrastructure side. It’s AI Agent Control Plane (ACP) provides comprehensive visibility and control over AI agents operating within the enterprise. They allow visibility into every AI agent along with its associated NHIs and machine credentials (including API keys, service accounts, secrets, and more). They are able to enforce AI agent with short-lived, precisely scoped credentials and just-in-time access based on least privilege principles, eliminating access chaos and reducing compliance risk.
Governance & Lifecycle Layer
On the authorization side, the most damaging breaches rarely result from a single failed login. They stem from standing privileges, coarse-grained roles, and ungoverned entitlements that allow a compromised identity to escalate privileges and move laterally across systems.
The governance layer is equally fragile. Gaps in joiner–mover–leaver (JML) processes leave behind orphaned and dormant accounts scattered across directories and SaaS environments. External guests often retain access long after their business purpose has ended, and fragmented ownership means few organizations can confidently answer the fundamental question: who has access to what, and why?
These issues are further amplified by the surge in NHIs, including service accounts, workloads, API keys, and bots that now outnumber human users. These machine identities often possess broad, opaque permissions, embedded long-lived secrets, weak rotation practices, and unclear custodianship, making them prime targets for exploitation.
In practice, IAM, IGA, PAM, and cloud IAM each defend a slice of the puzzle. Yet without a unified identity data foundation that normalizes telemetry and correlates risk across these systems, organizations lack end-to-end visibility. The result is an inability to prioritize remediation or understand the true blast radius of a compromised identity.
A durable response is an identity-first architecture that treats identity as the control plane. This approach requires enterprises to:
- Continuously discover and map every identity, human and non-human, along with its entitlements, pathways, and secrets across AD, IdPs, cloud IAM, and SaaS.
- Automate full lifecycle governance for every entity through authoritative HR- and workflow-driven provisioning and deprovisioning, ongoing access certifications for high-risk accounts, enforced secret vaulting and rotation, automatic API key expiration, and attested ownership for each identity and credential.
- Eliminate long-lived privileges by enabling just-in-time (JIT) access for administrative and machine identities, while normalizing identity data to unify visibility and improve risk scoring.
- Expand phishing-resistant MFA and Identity Threat Detection and Response (ITDR) coverage across all access pathways.
- Institutionalize continuous certification and measurable outcomes, such as significant reductions in standing privilege and improved mean time to detect (MTTD) and mean time to respond (MTTR) to identity incidents.
The net effect is a shrinking of the identity attack surface and a disruption of lateral movement before it can escalate into material business impact. In short, it aligns enterprise defenses with where modern attackers actually operate: the identity layer. These identity-layer challenges bring us to the next evolution of PAM itself, a domain now transforming to secure both human and machine identities.
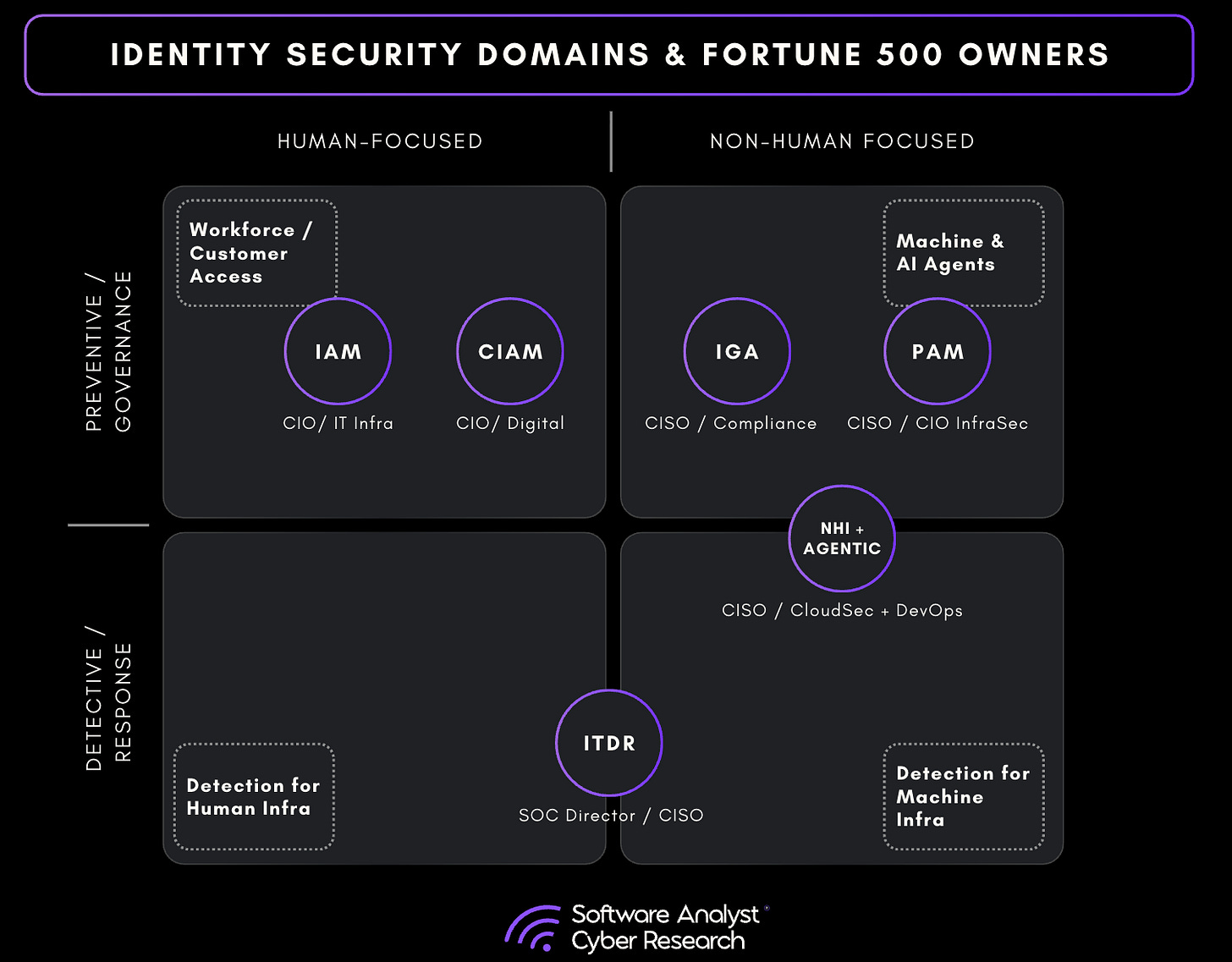
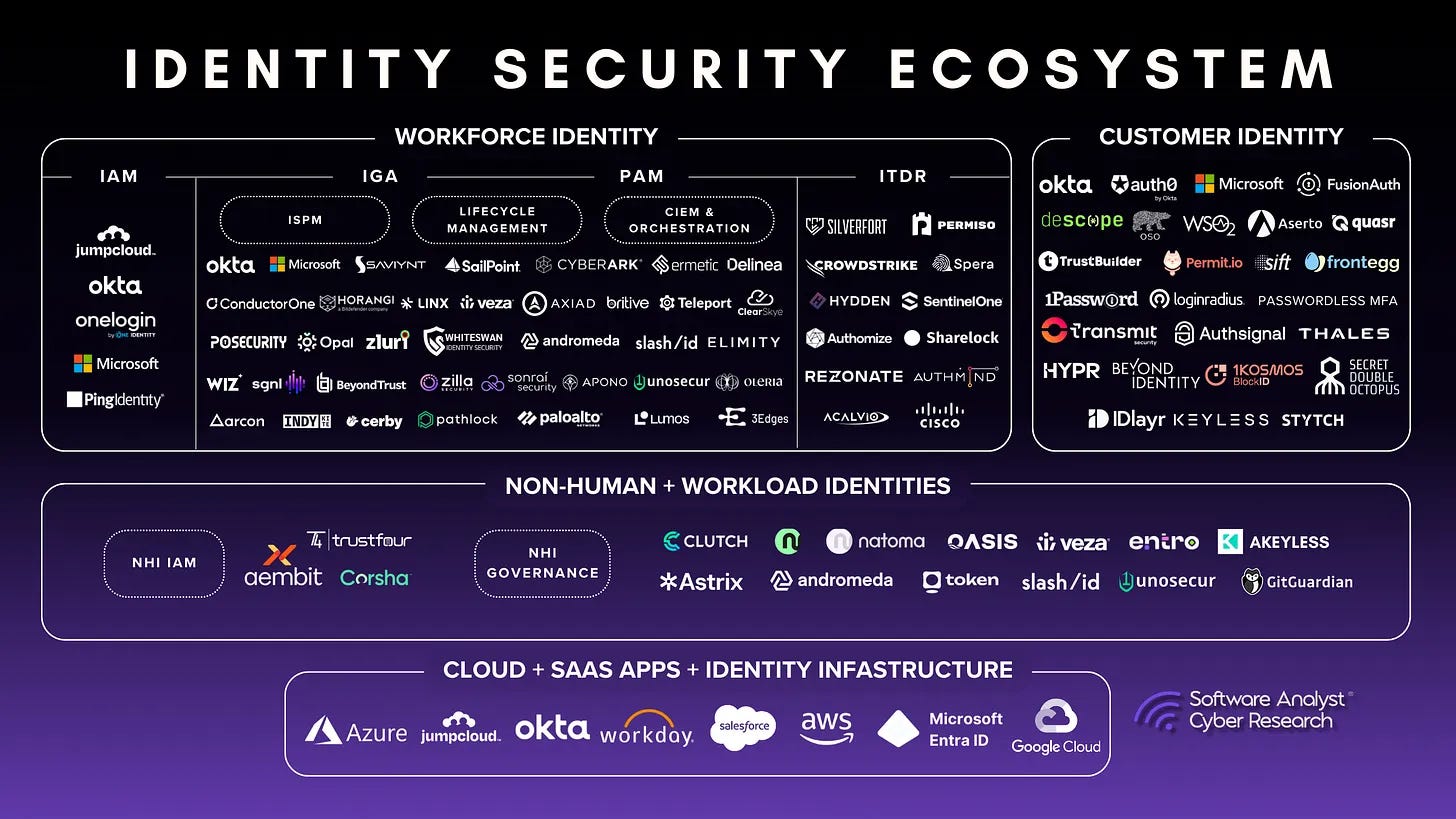
How Identity Is Bought & Sold In Enterprises
This is a depiction for how identity security domains are bought / sold within enterprises:
The Future of PAM: The Implications for the Future of PAM
The role of PAM is evolving now at an unprecedented pace. Traditionally, PAM focused on securing and auditing access to sensitive systems by human administrators. However, the explosion of non-human identities, ranging from microservices to autonomous AI agents, has fundamentally changed the landscape.
CyberArk’s long-standing leadership explains why PAM became a cornerstone of enterprise security architecture. However, the very category it helped define is now being recast for a new era. Modern PAM must extend far beyond password vaulting and session recording to enable ephemeral, JIT access not only for human users but also for dynamic, machine-driven entities that operate autonomously across hybrid and multi-cloud environments.
Secrets management, certificate lifecycle automation, and granular zero-trust authorization are becoming table stakes. The integration of PAM with broader identity security platforms is necessary to enforce least-privilege access policies across all users and entities, human or otherwise. This is particularly crucial as agentic AI systems become operational, introducing new attack surfaces that require robust privileged access controls. These systems require the same rigor once reserved for human administrators: controlled access, continuous monitoring, and context-aware revocation. The future of PAM will therefore depend on its ability to integrate with identity, governance, and detection systems, ensuring that privilege, regardless of where it resides, is both visible and governable in real time.

With PAM extending into these domains, the real question becomes how Palo Alto and CyberArk can bring their strengths together.
The most significant players within next-gen PAM to watch include:
- Silverfort extends PAM principles into authentication by unifying access control across on-prem, cloud, and hybrid environments without agents. Its architecture integrates directly with identity providers and directories to deliver adaptive MFA and conditional access for both privileged and non-privileged accounts. It helps close MFA gaps across legacy protocols and command-line interfaces.
- Apono focuses on dynamic JIT privilege orchestration. The platform automates access approvals and enforces time-bound permissions across infrastructure and SaaS environments. With integrations into tools like Okta, AWS, and GitHub, Apono enables DevOps and engineering teams to request and receive access instantly without manual intervention.
- Teleport takes a developer-first approach to secure access for engineers and workloads. Its unified platform handles authentication, authorization, and audit for SSH, Kubernetes, databases, and web applications using short-lived certificates instead of passwords or static keys. This certificate-based model fits naturally within modern zero-trust architectures.
Some general companies with strong PAM capabilities include Okta and Britive on the market.
Synergies & Challenges From Both Companies
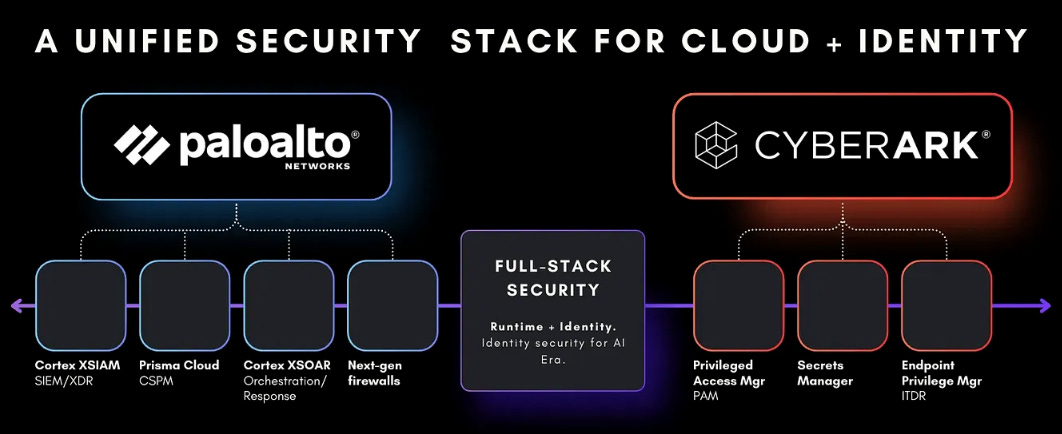
Futuristic SOC + Identity Platform
For broader security, integrating PANW and CyberArk’s identities will create a larger, more integrated identity business that is more deeply embedded in the SOC.
From a broader security standpoint, the integration of Palo Alto’s platform with CyberArk’s identity and privilege expertise signals the emergence of a next-generation SOC and identity platform. This convergence will create one of the most comprehensive and integrated identity ecosystems in the market – deeply embedded within the SOC and aligned with how modern enterprises detect, respond to, and manage threats
By incorporating PAM capabilities into a full-stack SOC architecture, organizations can begin to operationalize zero-trust privilege models at scale. This means unified visibility and control across both human and machine identities, regardless of environment or context. It also positions the combined entity to address the security challenges posed by agentic AI.
As autonomous systems increasingly drive enterprise operations, organizations will need foundational controls that extend least-privilege principles to workloads, bots, and AI agents.
The merger between Palo Alto and CyberArk deliver foundational, identity-centric controls that extend across every access surface. In doing so, they lay the groundwork for the future SOC, where identity becomes both the control plane and the intelligence layer of enterprise defense.
GTM wins & Cross-selling challenges
From a GTM perspective, the cross-sell opportunity created by the merger is substantial. CyberArk’s customer base of over 8,000 enterprises, combined with Palo Alto Networks’ nearly 70,000 customers, presents one of the largest potential commercial synergies in the cybersecurity industry. On paper, this alignment offers the chance to expand wallet share across both existing customer ecosystems
However, realizing this opportunity will be far from straightforward. CyberArk’s customers, particularly those in regulated and security-mature industries, are often deeply loyal but also highly sensitive to pricing structures and product autonomy. Any perception that Palo Alto might impose bundled subscriptions or mandatory platform adoption could create friction. Customers wary of increased costs or reduced flexibility may resist integration efforts, undermining potential cross-sell momentum.
To avoid this, the combined company will need to pursue a measured, customer-centric GTM strategy. Rather than enforcing consolidation through bundling, it should design licensing structures that emphasize flexibility and customer choice. Success will depend not on aggressive packaging, but on demonstrating the incremental value that unified identity and security operations deliver when working together.
Stability vs. Speed
The history of large-scale technology mergers demonstrates a consistent pattern: confidence is lost not when innovation slows, but when stability wavers. Delays in product releases, extended support queues, or inconsistent communication can quickly erode customer trust, particularly among enterprises that depend on security platforms for mission-critical operations.
In the context of the Palo Alto – CyberArk merger, stability will matter more than speed. CISOs and security leaders prioritize reliability over rapid change; they need assurance that the systems underpinning their identity and security operations will remain dependable, predictable, and fully supported.
One of the most immediate risks in any acquisition of this scale is the erosion of operational stability. Customers who have spent years tuning, integrating, and building workflows around both Palo Alto and CyberArk technologies will be acutely sensitive to even minor disruptions such as changes to product roadmaps, API behaviors, or support models.
Cultural & Ecosystem Integration
The challenges ahead are not limited to customers. They extend deep within the organizations themselves. Integrating Palo Alto’s network-centric, AI-driven SOC culture with CyberArk’s identity-first philosophy will require deliberate and sustained effort. The two companies bring complementary but distinct operating models, technical priorities, and go-to-market approaches. Aligning these without losing the unique strengths of each will be one of the merger’s most critical leadership tests.
Beyond culture, practical challenges remain. Product overlap, roadmap synchronization, and customer migration from point solutions to a unified platform will demand careful orchestration. Shifting customer perception from two specialized vendors to a single, full-spectrum security provider is a complex process, especially in a market where many enterprises are already deeply invested in competing ecosystems such as Microsoft or CrowdStrike.
The lesson from other industry mergers applies here as well: confidence can erode quickly when integration is poorly communicated or execution falters. Delays in product releases, increased service friction, or inconsistent messaging can rapidly undermine trust among customers and partners alike. Palo Alto would benefit from proactively signaling continuity, showing customers not only how the platforms will evolve together, but also how their current investments will remain protected and supported.
Preserving the Depth of CyberArk’s Specialization
CyberArk’s reputation has been built on its relentless focus on privileged access management. Its customers value that precision because PAM is a control domain where “good enough” can mean significant exposure. As Palo Alto brings CyberArk into its broader portfolio, there is a risk that the sharpness of CyberArk’s specialization gets dulled by attempts to streamline or bundle features into a larger platform experience.
What the Acquisition Means for Cybersecurity (Broadly)
Consolidation vs. Best of Breed
The Palo Alto Networks & CyberArk merger exemplifies a broader market shift toward consolidation and platformization in cybersecurity. As organizations contend with tool sprawl, fragmented telemetry, and escalating operational complexity, many are gravitating toward unified platforms capable of delivering end-to-end protection across network, cloud, endpoint, and identity domains.
This acquisition follows a trend set by other large-scale deals such as Google’s acquisition of Wiz and Cisco’s purchase of Splunk, each reflecting a strategic imperative to simplify security operations and improve efficiency through platform integration. The market momentum suggests that large, multi-domain security providers will increasingly shape the architectural blueprint of enterprise defense.
That said, CISOs and security leaders remain pragmatic. They value flexibility and the ability to tailor architectures to their organizations’ unique risk models. While Palo Alto’s unified platform vision is strategically coherent, it will only succeed if it respects customer autonomy. Enterprises that have invested heavily in best-of-breed solutions may resist if they perceive consolidation as forcing them to abandon specialized tools in favor of proprietary alternatives.
To balance these competing forces, Palo Alto will need to frame its platform not as a mandate, but as an option;one that reduces friction, enhances interoperability, and simplifies operations without constraining architectural choice. The vendors that win the next phase of cybersecurity platformization will be those that combine breadth and integration with openness and trust.
Conclusion
The Palo Alto Networks – CyberArk acquisition marks a defining moment in the evolution of enterprise security. It represents more than a merger between two leading cybersecurity vendors. It signals the beginning of a shift toward unified, identity-first platforms that integrate access control and response across every layer of the enterprise.
In today’s landscape, identity has become the new perimeter, and PAM has emerged as the critical bridge connecting human and machine access. The combination of Palo Alto Networks’ strengths in network, cloud, and SOC security with CyberArk’s leadership in identity and privilege management, now expanded to include the rapidly growing domain of non-human identities, creates one of the most comprehensive and interesting security platforms in the market.
This convergence sets the stage for a new competitive frontier which will be an interesting wedge to watch moving forward. The dynamics among Microsoft, CrowdStrike, Palo Alto Networks, and other major cybersecurity platforms will increasingly shape how enterprises architect their defenses. As these ecosystems evolve, large-scale, integrated platforms will define the next decade of cybersecurity.
The industry will be watching closely as Palo Alto and CyberArk integrate their technologies, align their cultures, and innovate at scale. Their success or failure will influence not only how enterprises secure privileged access, but how the entire industry reimagines the balance between identity, automation, and trust in the age of AI-driven security.


