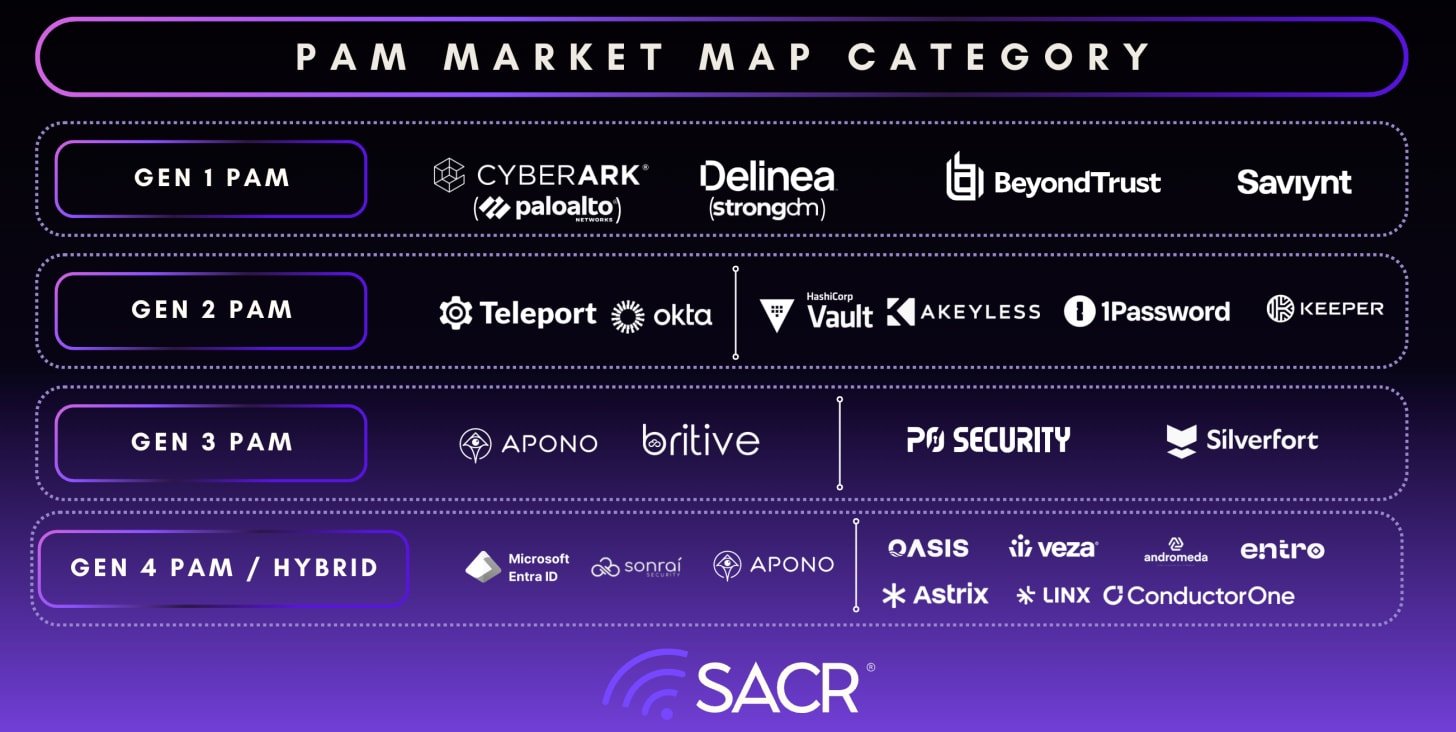
The Evolution of the Privileged Access Management (PAM) Market & The New Competitive Landscape
Introductory Blurb As Identity becomes central to agentic security, Privileged Access Management (PAM) is undergoing a structural shift. It is

Introductory Blurb As Identity becomes central to agentic security, Privileged Access Management (PAM) is undergoing a structural shift. It is
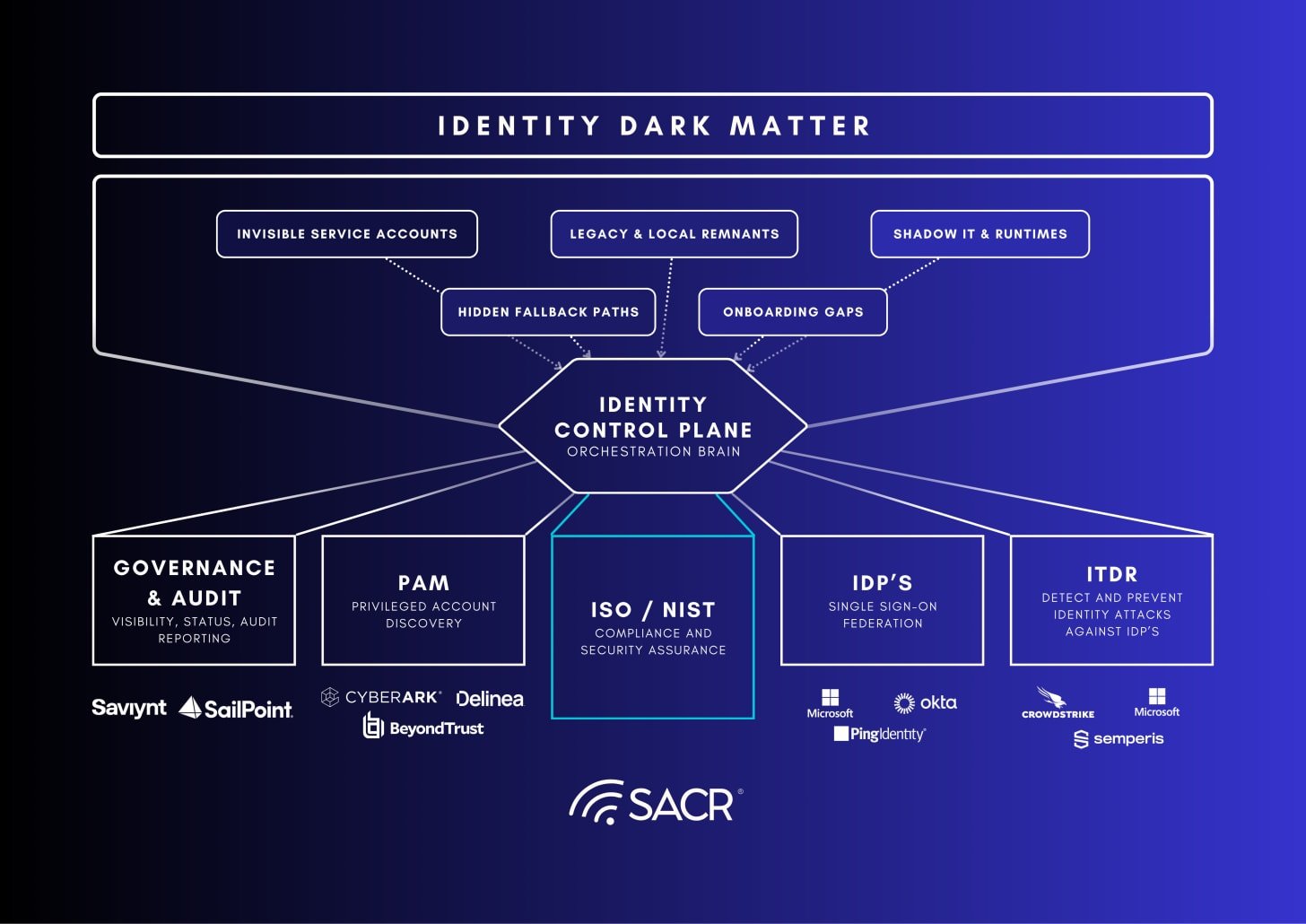
Actionable Summary Despite decades of investment in IAM, IGA, and PAM, enterprises remain highly vulnerable to identity-based attacks. The root
Author Aqsa Taylor is the Chief Research Officer at Software Analyst Cyber Research, where she leads research initiatives and the
Overview This report examines a blueprint for how a company can evolve from consumer password management into a credible enterprise

Readers, Today, we focus on the challenges organizations face when managing Identity governance and administration (IGA) and entitlements. As identity
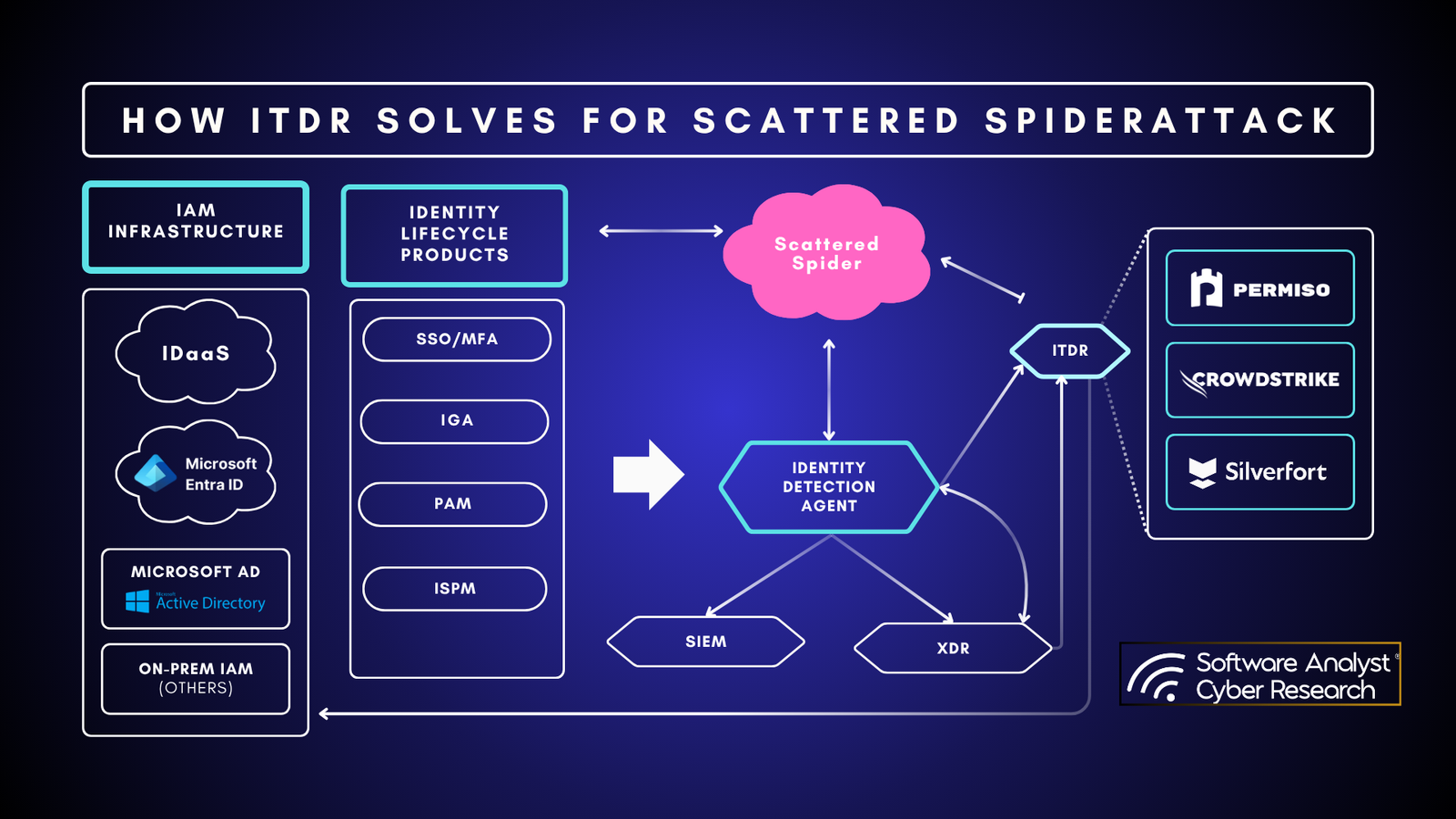
Today’s Report Structure SACR has a broad thesis about identity security becoming one of the biggest opportunities in cybersecurity. Over
Subscribe for a weekly digest on the best private technology companies.