We explore the newest frontiers of cybersecurity.
Whether you’re looking at emerging vendors, evolving threats, or shifting architectures, our timely, opinionated insights help modern security leaders make smarter, faster decisions.
Explore our research
We explore the newest frontiers of cybersecurity.
Whether you’re looking at emerging vendors, evolving threats, or shifting architectures, our timely, opinionated insights help modern security leaders make smarter, faster decisions.
Explore our research
Featured report

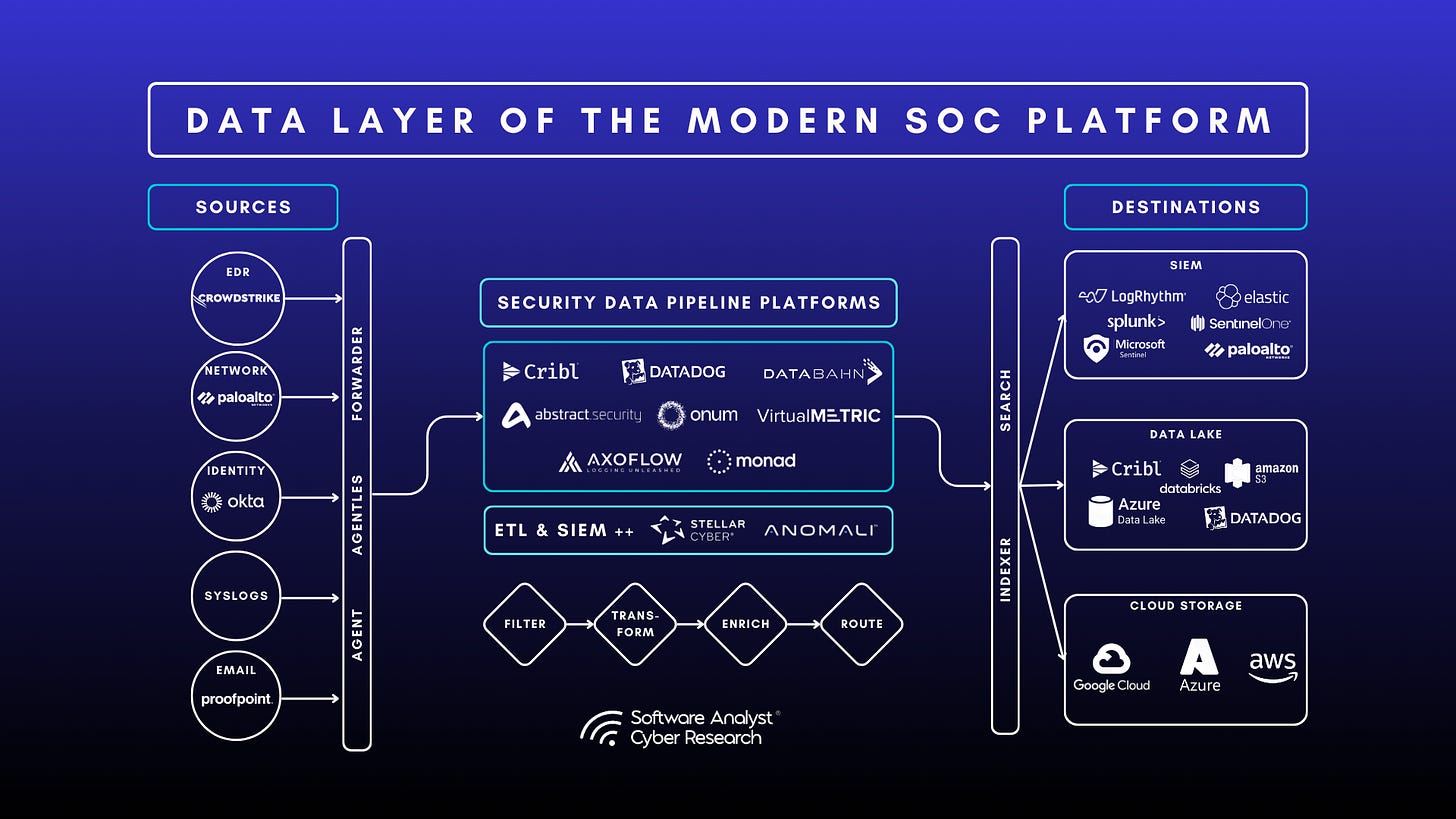
What CISOs Need to Know About the Modern SOC Data Layer: How Security Data Pipelines Improve Telemetry, Reduce Spend, and Accelerate Detection.
The SDPP market is entering a rapid consolidation phase as major SIEM, XDR, and observability providers acquire pipeline platforms to strengthen their data architectures. Recent deals include… Read more
Featured report

Why Identity, SaaS, and Cloud Now Define the Modern Attack Surface and How Leading Vendors Are Detecting and Responding to Scattered Spider (LUCR-3).
Organizations today are facing a rapid escalation in identity-centric threats driven by highly capable, financially motivated adversaries. Among the most disruptive is Scattered Spider (UNC3944/Octo Tempest), a cybercrime group whose… Read more
Featured report
This report is a comprehensive view of the 2025 AI SOC market detailing emerging trends within security, architectural options, themes, key vendors to watch and decision frameworks to guide leaders.
Over the past year, one of the most hyped and most-talked about sectors in cybersecurity has been the SOC, specifically the push towards the “AI‑SOC”, built on the premise of… Read more
The speed of recent developments in AI has been mind-blowing since the start of 2025. The primary barriers to widespread enterprise AI adoption involve balancing multiple considerations, including cost, risks of hallucinations, and security concerns.
AI has brought significant change and opportunity to enterprises. In 2023, AI emerged and some organizations became early adopters. In 2024, a significant increase in enterprise AI adoption occurred, but nothing previously…Read more

A practical roadmap for CISOs modernizing the SOC data layer: How security data pipelines are redefining SIEM economics and laying the groundwork for the future Security Operations Center (SOC)
Francis
Over the past year, one of the most hyped and most-talked about sectors in cybersecurity has been the SOC, specifically the push towards the “AI‑SOC”, built on the premise of LLMs triaging security alerts and automating… Read more
Subscribe for a weekly digest on the best private technology companies.